Applying cybersecurity automation to human cyber risk
Automated, real-time, and personalized workflows
As a security professional managing human risk, how long do you spend on manual, repetitive tasks?
Do you struggle to personalize security guidance for more and more people?
And do you wish you could automate day-to-day tasks to help you get more done?
You’re not alone. It’s hard for anyone to keep up. It’s boring. It’s stressful. And…it doesn’t help your people with the help they need.
We hear it all too often, cybersecurity professionals typically find:
-
- Managing and recording the many moving parts of a security awareness, behavior, and culture program is challenging.
- Programs demand considerable time and effort from people or teams that are frequently under-resourced.
- Many tasks are manual, repetitive, tedious, and time consuming.
- The growing number of systems you need to use can sometimes lead to mistakes or omissions.
We’d venture this has all started to feel normal. But normal doesn’t mean safe. Nor does it mean sustainable.
So, we’re rewriting the narrative.
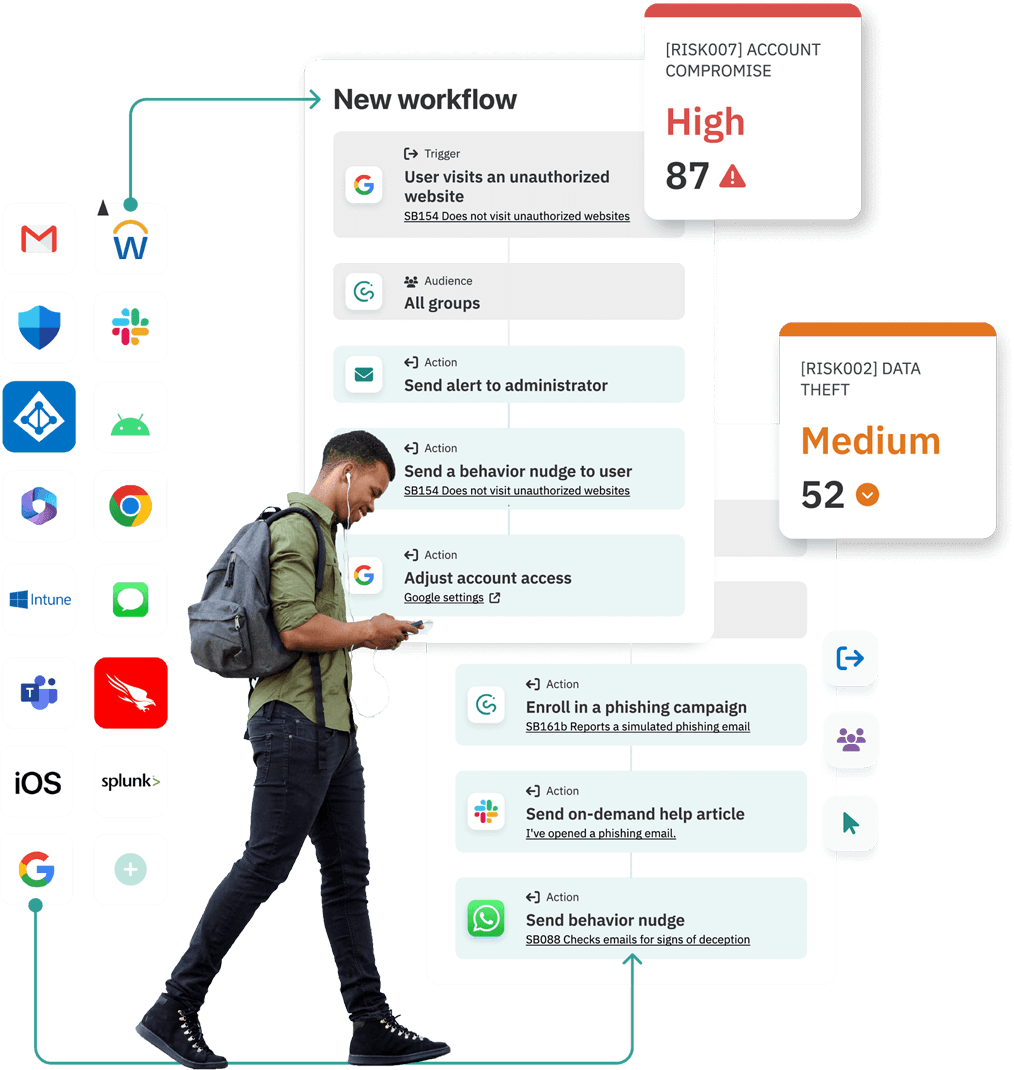
Introducing Workflows
Workflows. It’s our human risk management automation tool that lets you automate virtually any of your organization’s human risk management and security awareness tasks—without code!
It changes a lot. We’ll walk through how shortly. First let’s make sure we’re on the same page about the linchpin of this whole thing—automation.
Cybersecurity automation:
What it is, and what does it do?
Cybersecurity automation was once a snazzy “nice to have”. That becomes less of the case every day.
With access to more data, with more interconnected tools on hand, and with budgets for people being squeezed (whilst budgets for tech remain healthy) automation is becoming a “table stakes” component of any human risk management strategy.
Cybersecurity automation boils down to the strategic use of tools and data. It’s about harnessing tech to:
-
- Automate repetitive tasks
- Personalize controls and communications
- Accelerate response times
PART 2
Cybersecurity automation
Use cases
1. Personalize learning: Workflows allow personalized communication to groups and audiences based on skill levels, region, seniority, and risk.
2. Support joiners, movers, & leavers: Automate cybersecurity messages, guidance, and support for groups including new joiners, people changing roles or departments, and colleagues leaving your organization.
3. Support generative AI security & governance: Workflows automate sending nudges, guidance, and support for people who might be using LLMs inappropriately (or inefficiently).spreadsheet, workflows efficiently connect third party systems and reduce the time and effort you’d normally spend on everyday tasks.
1. Reduce phishing risk: Turn phishing missteps into teachable moments. Workflows automate phishing-related behavior nudges, and enroll users into tailored learning campaigns based on simulated phishing results.
2. Deliver timely help: Timing is crucial in learning. With Workflows, learning content is not just relevant, but also timely. Scheduling means people get the right information at the right time, reducing information overload and boosting retention.
3. Engage & support leadership: Frequent updates to managers consume time. Workflows send automated alerts, messages, and notifications to team leaders and executives across your organization, helping them to support security efforts and take responsibility for employee-related cybersecurity in their teams.
1. React quickly to incidents: Workflows act as an automated assistant, allowing actions to be automated across a growing number of software tools. Whether it’s resetting compromised passwords, logging tickets in Jira, or automating entries into a spreadsheet, workflows efficiently connect third party systems and reduce the time and effort you’d normally spend on everyday tasks.
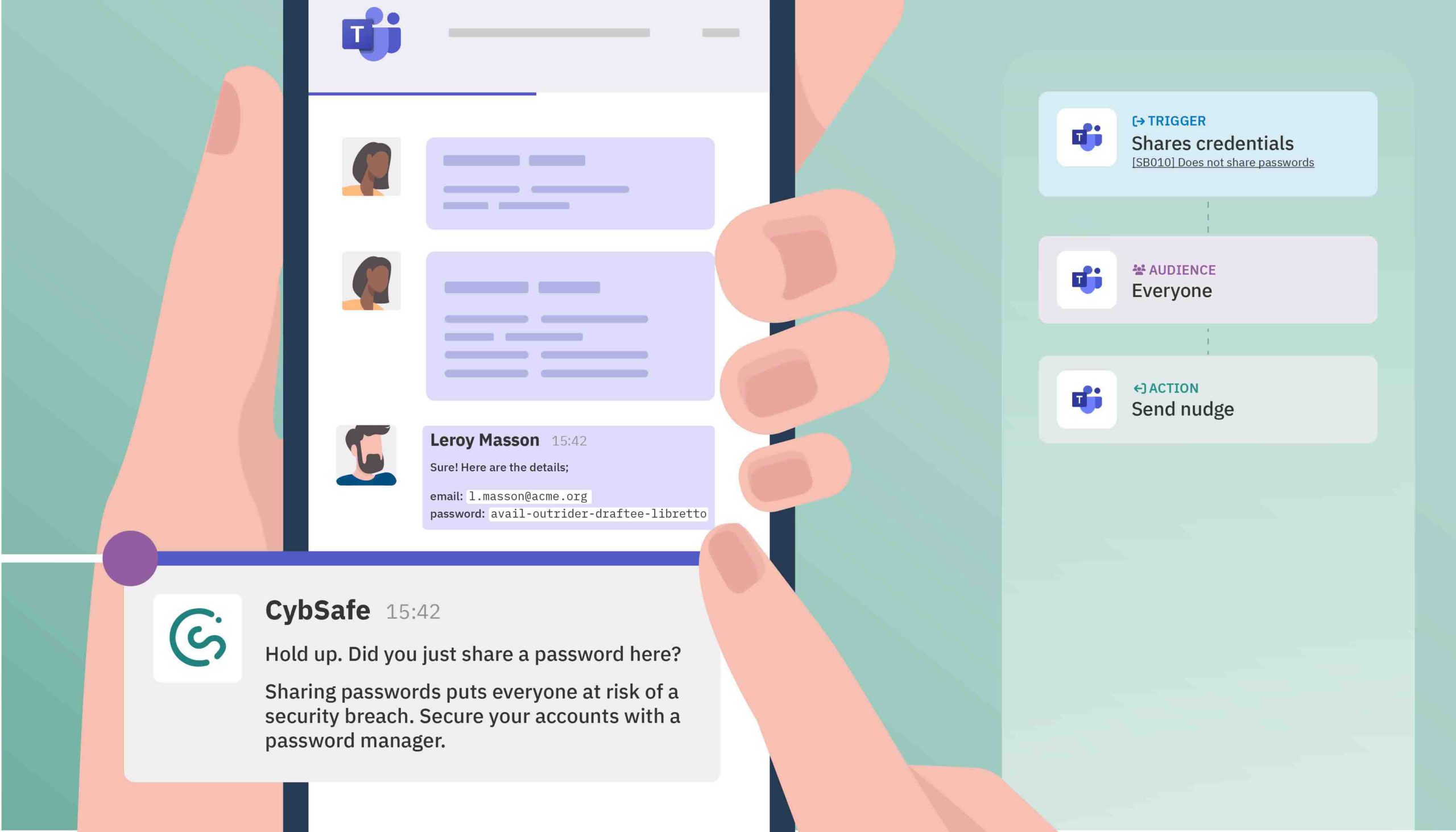
2. Influence security habits: Swift interventions are often key to improving security behaviors. If a user slips, like sharing sensitive credentials, workflows send automated and personalized messages. It’s like a one-to-one security lesson, getting them quickly back on course.
Security automation will never replace human expertise. But it does free you up to focus your expertise on the things only you can do. So teams work smarter and more efficiently, and can give more focus to strategic initiatives.
PART 2
Cybersecurity automation
Cybersecurity automation vs. cybersecurity orchestration: What’s the difference?
Cybersecurity orchestration and cybersecurity automation are closely related, but they’re not the same.
Cybersecurity automation involves using technology to execute predefined, repetitive tasks without human intervention.
Cybersecurity orchestration, meanwhile, goes a step further. It involves integrating multiple technologies, tools, data, and processes to create a cohesive response to threats.
Security Orchestration, Automation, and Response (SOAR)
Security orchestration, automation, and response (SOAR) is a comprehensive approach to cybersecurity operations that combines—you’ve guessed it—orchestration, automation, and response.
The complexity and volume of cyber threats is constantly increasing. Vitally, SOAR provides a systematic and efficient way to manage security incidents.
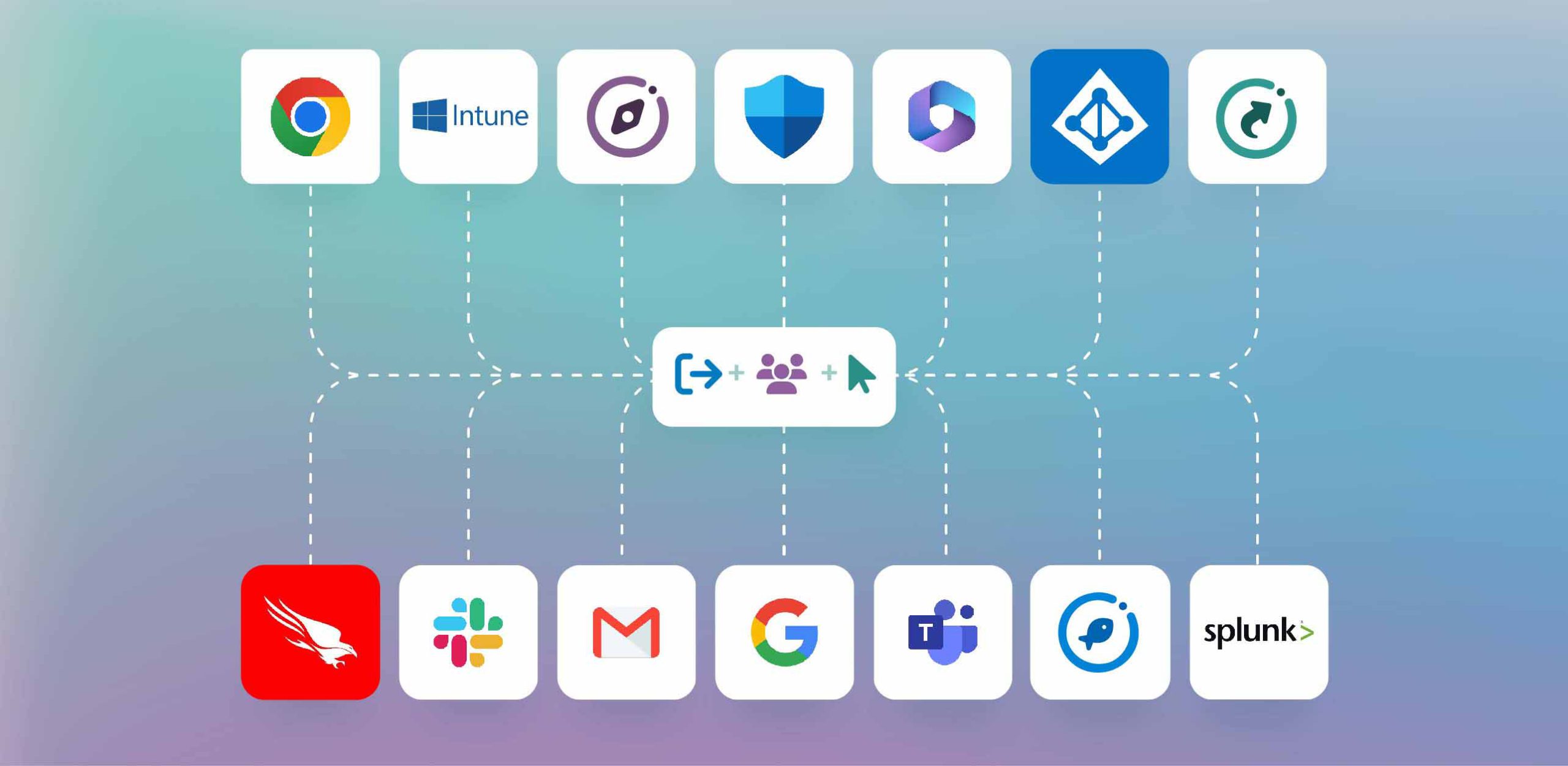
CybSafe RESPOND aligns with the principles of SOAR. It leverages risk data, automates security interventions, and establishes intelligent workflows triggered by behavior events and security incidents.
RESPOND focuses on quantifying human risk, automating responses, and integrating third-party data sources and tools. This enhances behavior intelligence, making it a vital component for human risk management in cybersecurity.
And now, we’ve brought Workflows to the party, too.
A leap forward in human risk management
Recent research from Gartner shows cybersecurity leaders have high hopes for their security awareness programs, yet underinvest in this space because legacy solutions do not meet current needs.
Less than half of cybersecurity teams measure employee behavior, and almost 80% have less than one FTE dedicated to security awareness.
The need for Workflows to support human risk management efforts was clear. When building Workflows, the CybSafe Product and Engineering teams worked towards three key principles.
PART 3
A leap forward in human risk management

1. Automation: Manage at scale
Cybersecurity automation allows small teams (or individuals) to manage security behavior at scale without a linear increase in workload or teamsize.
2. Real-time response: React instantly, improve security behaviors
Next up, real-time response. This is critical to human risk management’s evolution because it allows organizations to react instantly to threats and risky behaviors.
Real-time human risk response capabilities monitor people’s activity, detect threats, and alert the right people.
3. Personalized learning: Customize everything
Finally, the cherry on top. Personalized learning.
Give people their very own tailored learning paths, and you’ll see their knowledge, behavior, confidence, and engagement in cybersecurity improve. Give people bland tick-box training, and you won’t.
Getting started with Workflows
Let’s get stuck in and look at how workflows are built.

PART 4
Getting started
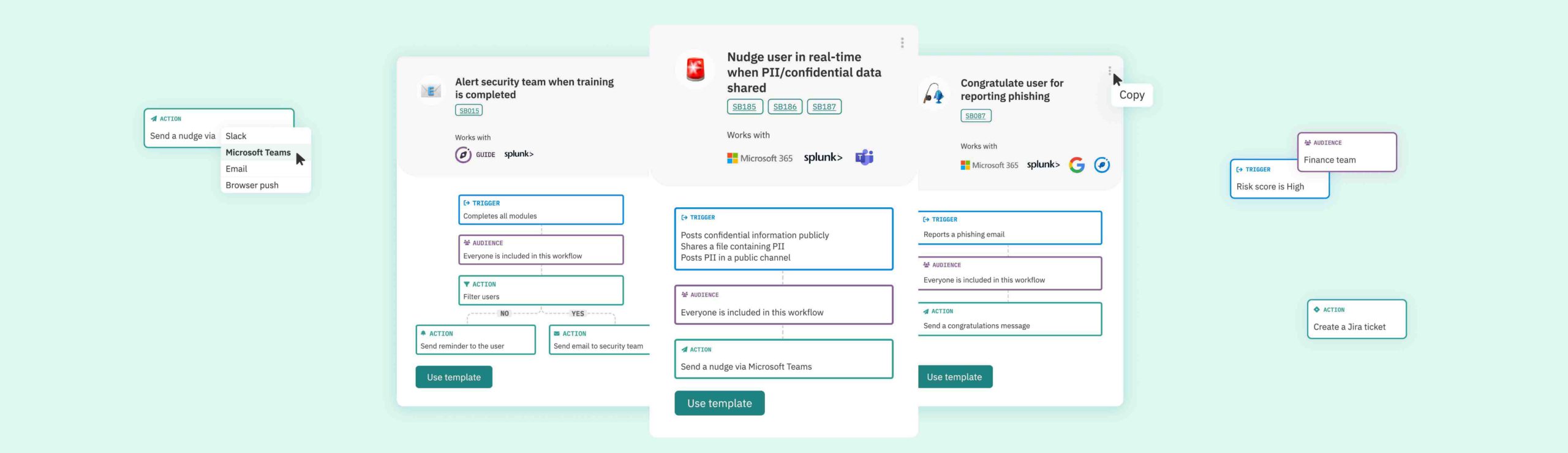
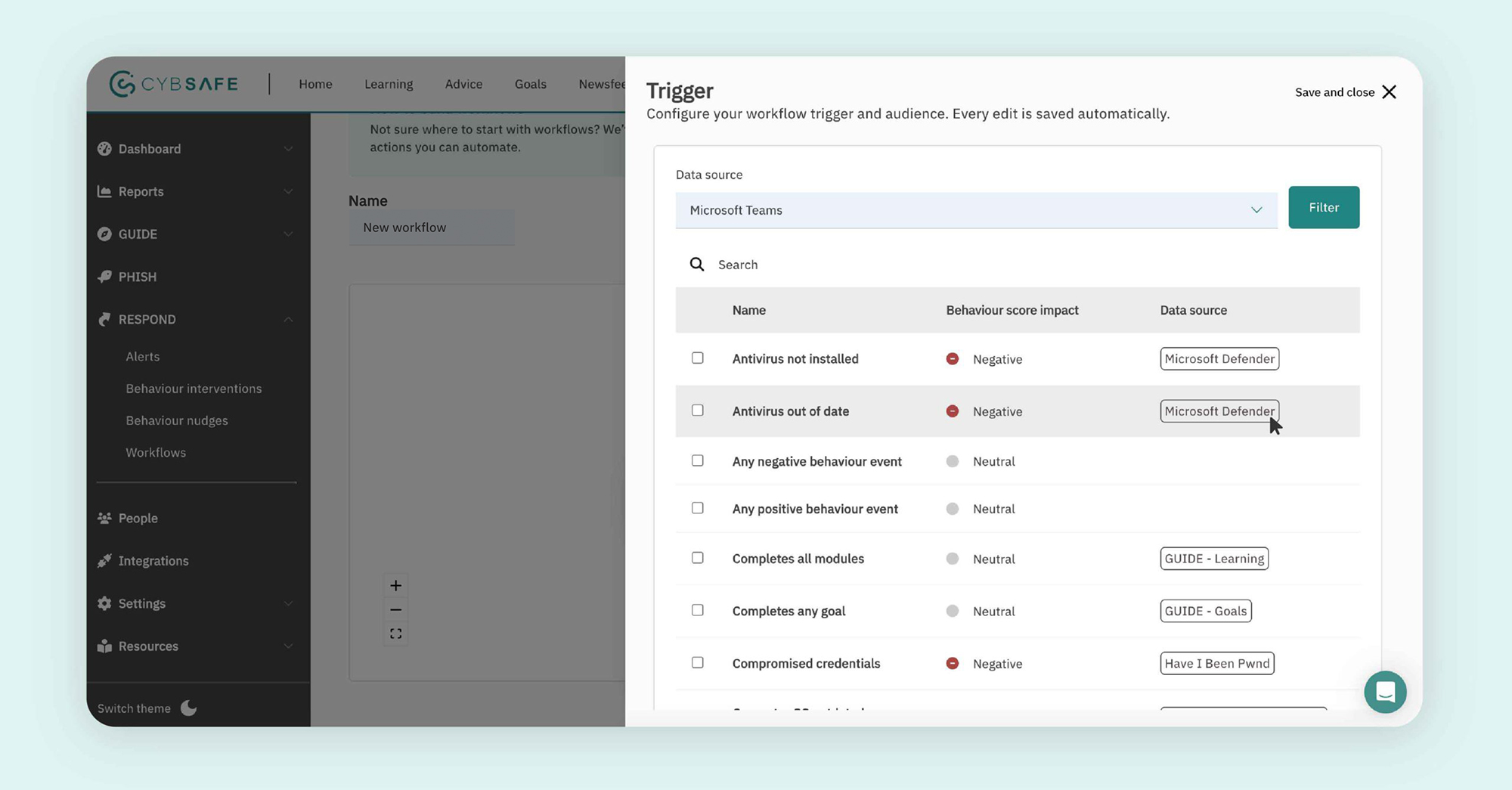
Step 1: Trigger
The Trigger function determines when the Action (selected in step 3) will activate.
Triggers are selected based on activity taking place within the CybSafe platform, or any one of a number of integrated systems. For example:
-
- In-platform activity: User completes a selected goal, user reports a phishing message, or user enters data into a simulated phishing landing page.
- Integrated system activity: User posts PII in a public Slack channel (Slack, Splunk, Microsoft 365 DLP), or user uses leaked credentials in a password (Azure AD Identity Protection).
CybSafe integrates with a number of workplace productivity and security tools. And we’re adding more all the time.
PART 4
Getting started
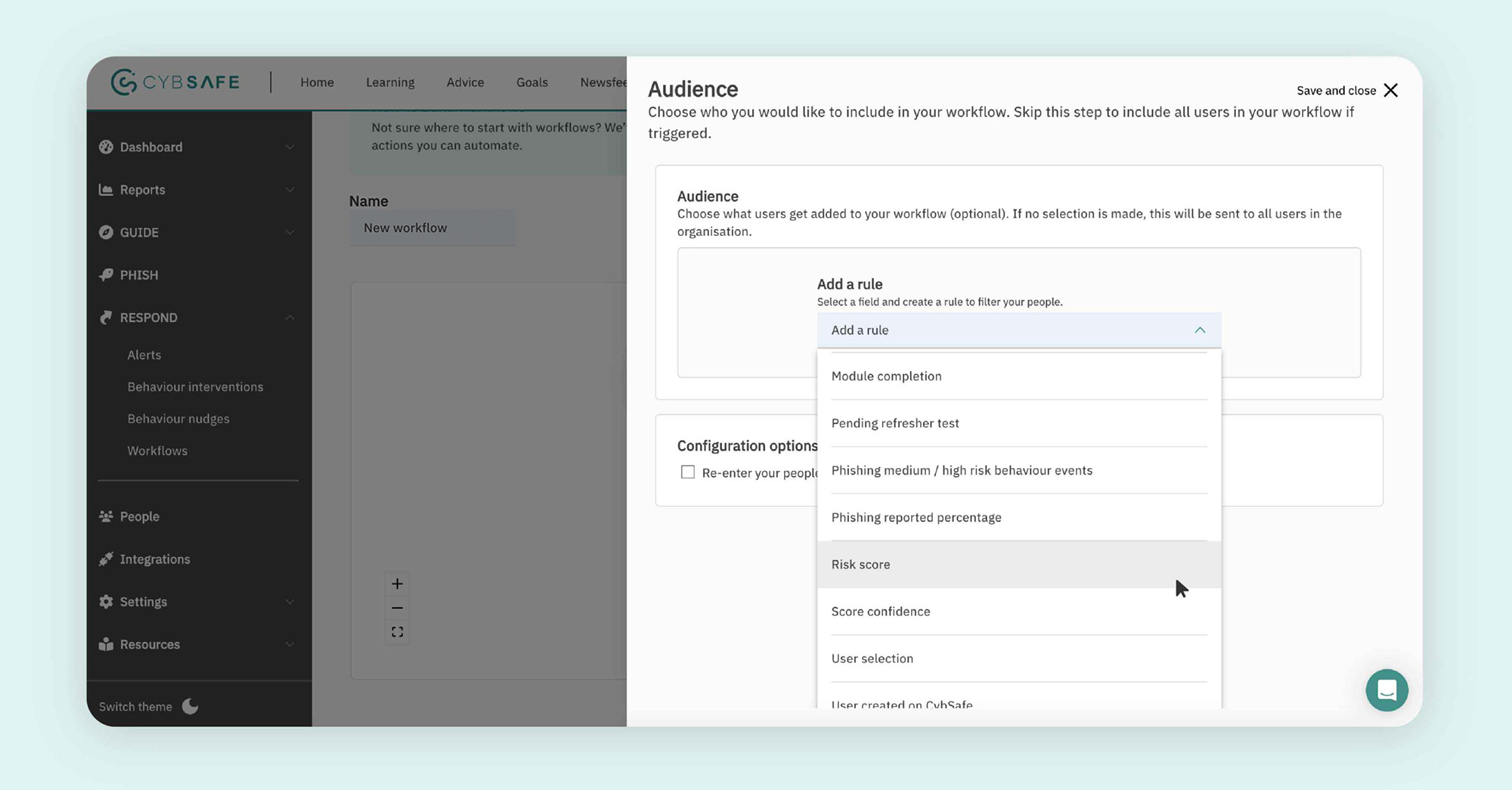
Step 2: Audience
The Audience function determines who will be enrolled into a workflow.
-
- User groups: Audiences can be selected based on predefined User Groups specific to your organization.
- Progress characteristics: Audiences may also be built based on progress such as the amount of training completed, the last time they logged in, or whether they have any pending refresher tests.
- Risk characteristics: Finally, and most notably, audiences can be selected based on risk characteristics, such as risk scores, phishing reporting percentages, and number of high-risk phishing actions.
You can, of course, combine any of the above to create an audience. For example, you might select anyone in your Finance Team, who have completed training modules, with a high risk score, to receive follow-up support.
PART 4
Getting started
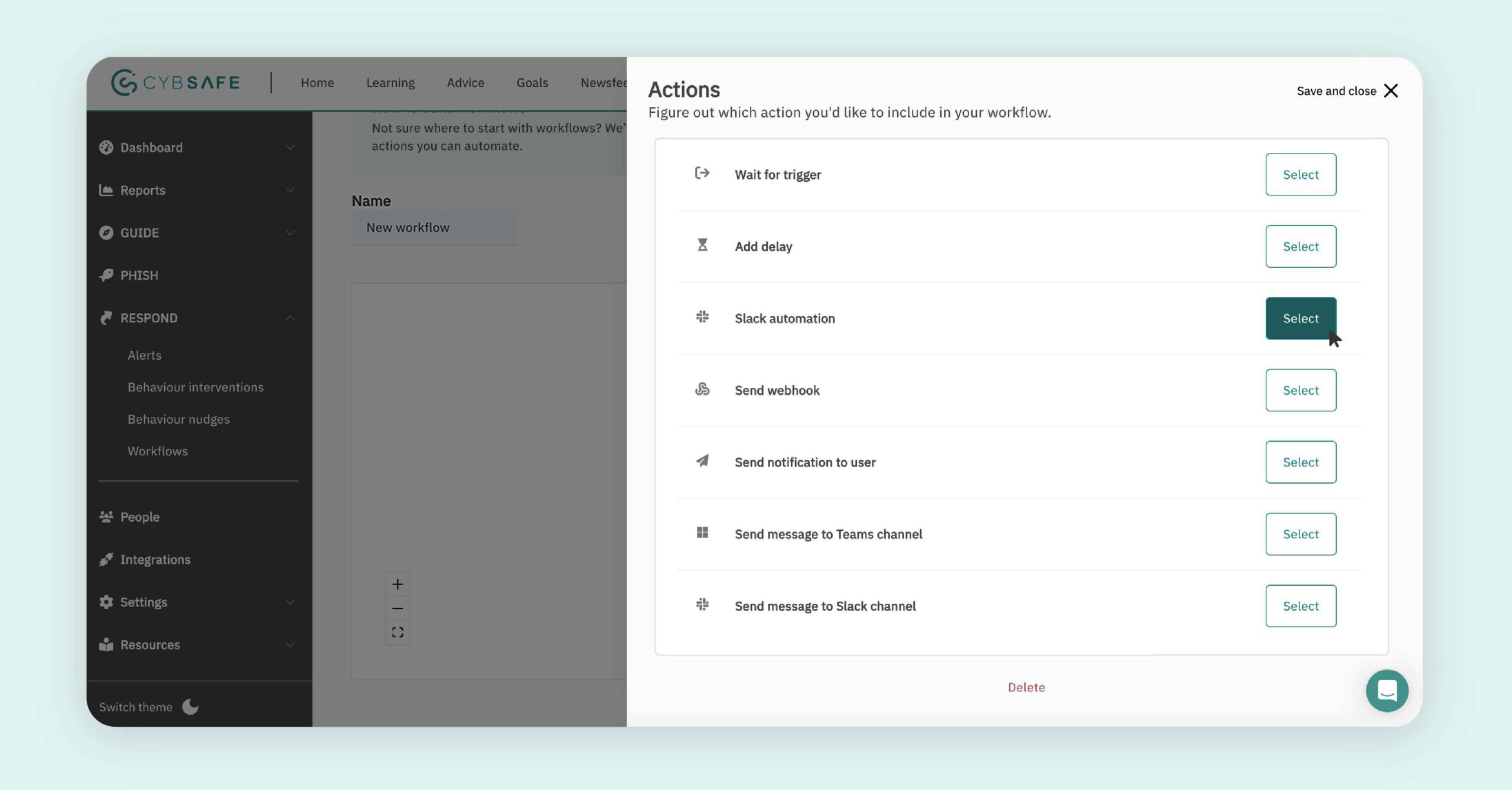
Step 3: Action
The Action function determines what your workflow will do.
We offer a range of actions to support personalized learning & comms, incident response, leadership notifications, and automated actions across your tech stack.
Notifications are received right into email, Slack, or Teams direct messages, where people are most likely to see and be swayed in a better direction.
Notable actions include:
-
- Enroll in training/simulated phishing: Enroll users into training and simulated phishing campaigns based on their activity.
- Send notifications: Send users and managers emails, CybSafe nudges, and Slack, Teams, & Google Workspace messages.
- Add/Remove user to groups: Add and Remove users to groups based on their activity.
- Filter users: Build different paths for people based on their actions and membership to groups.
- Send webhooks: Make HTTP requests to a specified URLs.
PART 4
Getting started
No coding required!
We know, it’s not like coding is some great mystery. Plenty of people can code. Maybe you’re one of them.
But it takes time. And effort. Hence why a Workflow is ridiculously simple to create.
Select a trigger. Choose the audience. Program the action. Done.
PART 4
Getting started
The Workflows library
The sheer number of possibilities presented by Workflows is overwhelming. Trust us, we did the math.
We’ll dive deep into the art of the possible in a future blog. For now, we’ve built a template library to get you started with the most popular workflows.
Turning work into Workflows
Cybersecurity demands considerable time and effort from teams who are frequently under-resourced.
Workflows automate tasks, react instantly, and provide personalized security help. This frees up time to focus on more strategic initiatives.
Gartner coined the term “cybersecurity mesh” to define the integrated approach that protects assets in a network, by building layers of security to connect all of the tools used across the network.
Turn your work into Workflows. Use them to make the most of the data and tools you already have at your disposal.
No more endless manual interventions or generic training modules. No coding. No sweat.
See how Workflows can transform your security awareness and human risk management programs. Schedule a demo today. We can’t wait to show you around.


