Criminals have a new way of spoofing URLs with Inception Bar Phishing
In certain circumstances, inception bar phishing can be extremely convincing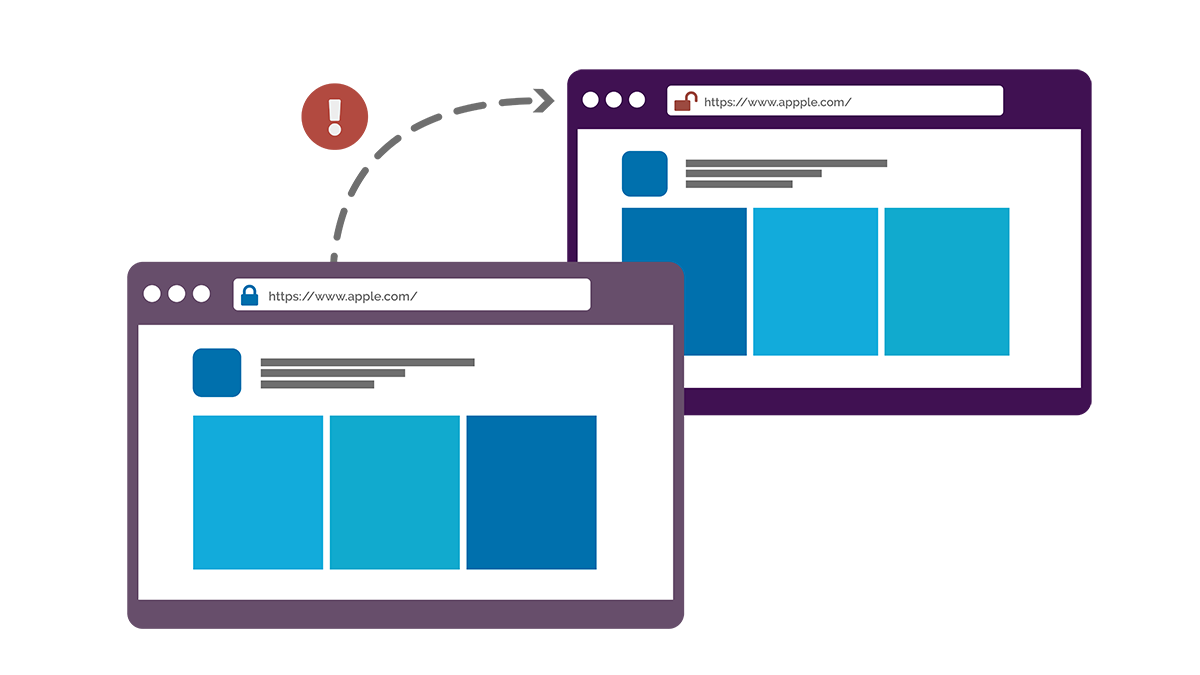
Although cyber criminals spoof URLs through various means, none are without their flaws. URLs such as amazzon.com, for example, are obvious to people-centric security cultures. Punycode URLs, meanwhile, are easily unmasked by modern browsers.
No matter how slick a cyber attack might be, a guilty URL often sees the campaign crumble. And that’s precisely what makes inception bar phishing such a menacing threat.
Inception bar phishing explained
In inception bar phishing attacks, fraudulent URLs are indistinguishable from the real thing – because the “inception bar” isn’t actually a URL bar at all. Instead, inception bars are (at a rudimentary level, at least) images.
Inception bars are typically configured to remain at the very top of browser windows. When a page first loads, users usually see two “URLs”: the real URL – say fakeurl.com – then the inception bar image, which might read societegenerale.fr.
Clearly, the presence of two URL bars signals suspicious activity. That is, unless you’re browsing using Google Chrome on a mobile phone or tablet.
When browsing in Chrome on a mobile device, the genuine URL is hidden once people begin scrolling down – leaving only the inception bar visible. And clever coding can ensure the genuine URL remains hidden for good. With the URL bar hidden, the trap is complete.
In theory, the tactic allows criminals to create fraudulent websites that offer no visual clues of their shady nature.
Preventing inception bar phishing
As concerning as inception bar phishing might be, the scam is far from bulletproof. The fact that inception bar sites “switch” URLs, for example, is a clear warning sign. What’s more, verification checks still overcome almost all social engineering attacks – inception bar phishing included.
Preventing the scam, then, requires alert, aware and empowered people, which is where technology can lend a hand.
While compliance-based, tick-box security awareness training might do little to enhance cyber resilience, both CybSafe and The Security Company have found role-based e-learning that adapts to prevent emerging threats can make people a very real cyber defence.
Going further, tools that measure and monitor cyber risk also have a role to play, allowing CISOs to respond to emerging threats accordingly.
The power of people and technology
As inception bar phishing takes advantage of the way in which the Chrome mobile app “hides” URLs, it’s likely the threat will fade as Chrome evolves. Even so, inception bar phishing highlights the ever-changing nature of the cyber threat landscape. Should inception bar phishing fade, other threats will emerge to take its place.
As always, by harnessing the power of people and technology, security professionals (and indeed societies) can combat cyber threats across the board.

