Influence long-term security behaviors
Apply more targeted interventions, and help people make better security decisions.
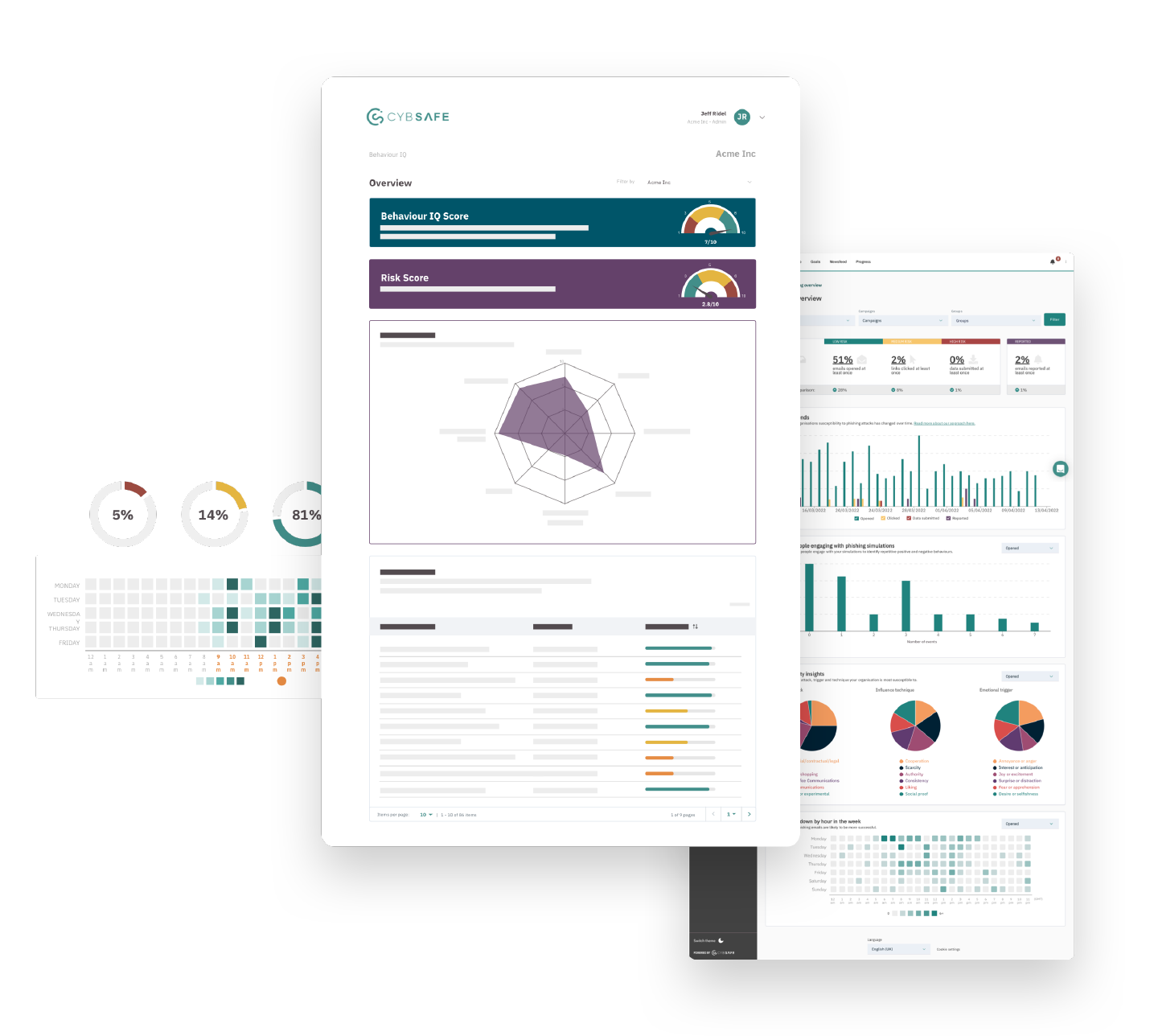
Measurably reduce your human cyber risk
A selection of purpose-built tools, features, and integrations.
Measure 100+ behaviors in a quarter of the time 84% with advanced behavior tracking and reporting tools that cut time and effort.
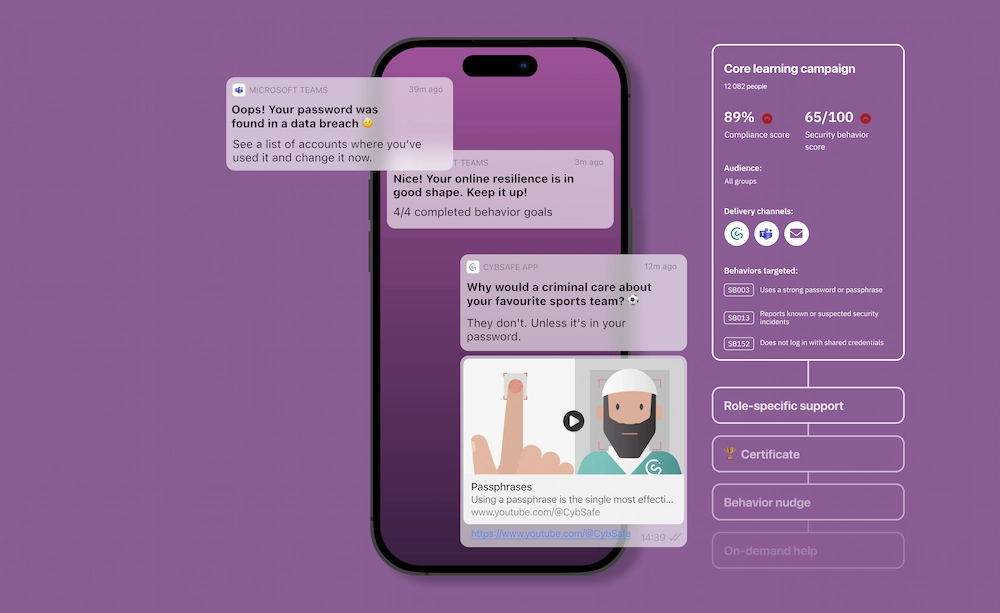
Target specific security behaviors
linked to your organization’s risks with a suite of behavior-oriented features.
Demonstrate behavior change and risk reduction with behavioral science-based measurements and reliable metrics.
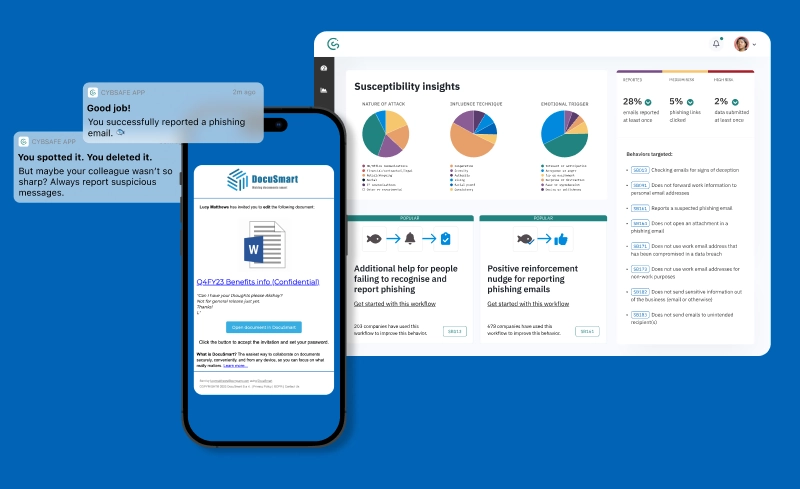
Quantify human cyber risk
Most organizations spend an average of 64 hours per month measuring 2 to 4 behaviors—resources that could be put towards risk reduction.
With CybSafe, you can measure 100+ security behaviors, 75% faster. That’s a reliable overview of your organization’s high-priority security behaviors in just 1 week.
Break down your human risk with:
Security behavior scores, to see the extent people engage in the specific security behaviors that matter to your organization.
Industry benchmarking, to show you how your organization compares to others.


Target behaviors, target risk
Most organizations believe they are reducing their human cyber risk because a cybersecurity vendor sold them a solution that purports to do just that. But more often than not, these ‘solutions’ don’t target behaviors—so they don’t reduce risk.
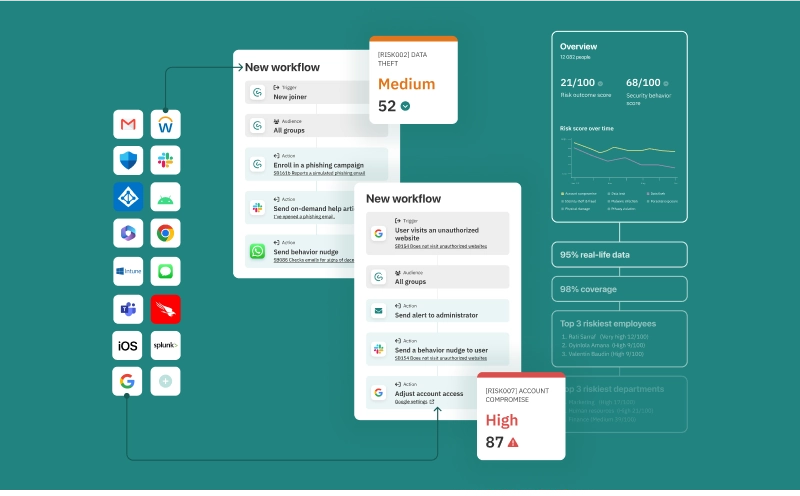
CybSafe gives you everything you need to identify and target the specific security behaviors linked to your organization’s risks. And it’s all backed by behavioral science.
Lower your human risk with:
Security behavior reports that give you a comprehensive, quantified view of your organization’s human cyber risk.
A behavior management engine that uses platform data and data from your security stack to coordinate automated, personalized support to each individual user.
Make proof painless
Whether it’s to meet compliance requirements, secure more resources, or garner support for security decisions—security professionals are under mounting pressure to prove risk reduction.
The CybSafe platform helps you make progress, and prove it. Measure the impact your interventions have on security behaviors, without the hassle.
Get the data you need with:
Comprehensive, intuitive reports that provide data about human cyber risk you can’t get anywhere else.
Customizable grouping so you can filter data by region, department, role, or different user groups.
Influence long-term security behaviors
And demonstrate risk reduction.
Our Products
More solutions
Achieve compliance, improve security awareness, & increase engagement
A scientific way to meet your security awareness training & compliance requirement and reduce human risk.
Assess security culture and promote positive behavior.
Understand and measure the factors that help you create a positive security culture.
Nudge & support people across multiple platforms.
Give people the push they need to act and provide real-time, frictionless help when they need it most.
Run phishing simulations that tell you what drives behaviors.
Find out why people click on, engage with, and report phishing emails—or why they don’t.
Security Behaviors FAQs
Get more insight

REPORT
Oh Behave! The Annual Cybersecurity Attitudes and Behaviours Report 2022
How much does attitude impact behaviour — and increase cyber security risk? To answer that question and more check CybSafe’s report.

WEBINAR
Influencing specific security behaviors: Real-world examples
If you’re not influencing security behaviors, then you’re not reducing risk. Find out all about the tools and resources you’ll need to do it.

WHITEPAPER
Behavior change: An intelligent approach for cyber security
Learn more about applying behavioral science to cyber security and how our products can help you drive behaviour change in employees.