Human risk management is…official!
Reflections on Forrester’s Human Risk Management Solutions Landscape, Q1 2024
Not another cybersecurity report!
We know. Stacks of reports slide into your inbox seemingly every day.
But Forrester’s recent take on the security scene got our attention at CybSafe (and, frankly, it should get yours, too).
“The Human Risk Management Solutions Landscape, Q1 2024” tracks—and makes the case for—a critical paradigm shift: moving beyond compliance-driven security awareness & training (SA&T), to human risk management (HRM).
We couldn’t agree more.
Human risk management is official.
At CybSafe, we believe in people. Human behavior is a factor in 74% of security incidents, after all.
If you improve people’s security behaviors, you reduce risk.
The problem (for decades, might we add) is the status quo does little to change behavior.
Only 15% of people who receive traditional SA&T actually go on to change their behavior.
Yes, the training was designed by humans, for humans. But if it doesn’t help people reduce their risk, it’s not human risk management.
In many ways, we believe Forrester’s recent report confirms what we’ve been saying for years: The future of security is human-centric.
Here, we’re unpacking what Forrester has to say, weighing in with CybSafe’s unique take, and laying down some bars on refining the thoughts and perceptions of HRM—and why that matters.
In fact, let’s start there.
Part 1: How we think about HRM matters (a lot)
Mindset.
Mindset fundamentally impacts how you approach HRM, and what HRM gives you in return.
In other words, perception affects implementation, which affects success.
How can CISOs and security awareness pros refine a HRM mindset to ensure it fosters a [solid] security posture in their organization?
As ever, we have thoughts.
(Speaking of which, if you haven’t read our definitive guide to human risk management yet, put it on your reading list, stat.)
PART 1
How we think about HRM matters (a lot).
“Doing” HRM
HRM is not something you “do”. HRM is an approach you take.
It’s a significant change of mindset, strategy, process, execution focus, and technology used to address an age-old problem in a new world: the management of cybersecurity risks posed by and to users.
PART 1
How we think about HRM matters (a lot).
What is HRM?
Forrester describes HRM as:
“… an evidence-based method to train people and initiate policy interventions based on their risk profile…solutions focus on changing behaviors and promoting a security culture.”
At CybSafe, we define HRM as:
“…the identification, evaluation, and prioritization of human cyber risks, followed by coordinated and effective application of resources to (A) minimize, monitor, and control the likelihood or impact of harmful cyber events, or (B) maximize the realization of digital opportunities.”
However, maybe the simplest definition of HRM is:
“…optimized management of cybersecurity risks posed by and to users.”
PART 1
How we think about HRM matters (a lot).
Where does security awareness & training (SA&T) and simulated phishing fit in?
Within HRM there are tactics and initiatives that together determine how effective your approach to HRM is. They also indicate the extent to which you are trying to adopt a HRM approach, (as opposed to a legacy SA&T, comms, and simulated phishing approach).
“Security Awareness” and “Security Awareness & Training” (SA&T) are umbrella terms for tactics or initiatives that might be included as part of an HRM program. These tactics include simulated phishing.
“woefully under-cooked”
However, human risk management programs that are made up primarily by these two initiatives are woefully under-cooked. Most importantly, they lack the ability to determine whether they are effective at reducing risk.
PART 1
How we think about HRM matters (a lot).
Fundamental principles
An individual, organization, or vendor cannot claim to have adopted an HRM approach without buying in to some fundamental principles –
-
- Measuring security behaviors to determine the effectiveness. Delivering security education, simulated phishing and awareness-raising activities are not enough. You need to identify and measure the user security behaviors you hope to influence in order to determine whether your HRM initiatives are effective.
- Focus on risk-outcomes not security awareness activity. HRM reporting should articulate changes to risk (or even better, risk-outcomes), rather than just training completion, or simulated phishing clicks/reporting.
- Evidence, data and outcomes. A HRM approach is evidence-based and data-driven. The desired outcomes are clear and measured. The evidence and data becomes the starting point for the next set of activities.
Image: SebDB. Security behavior data base
PART 1
How we think about HRM matters (a lot).
What makes HRM platforms different from legacy SA&T platforms?
In addition to educating and enabling the workforce to protect themselves and their organization against cyber attacks, and promoting a positive security culture, comprehensive HRM solutions do many (if not all) of the following:
-
- Detect, identify, and measure risky human security behaviors through integrations with a variety of data sources.
- Report on human risk factors beyond training and simulated phishing, and quantify human risk.
- Initiate, automate, and adapt policy, behavior, and training interventions in real time based on actual or perceived risk.
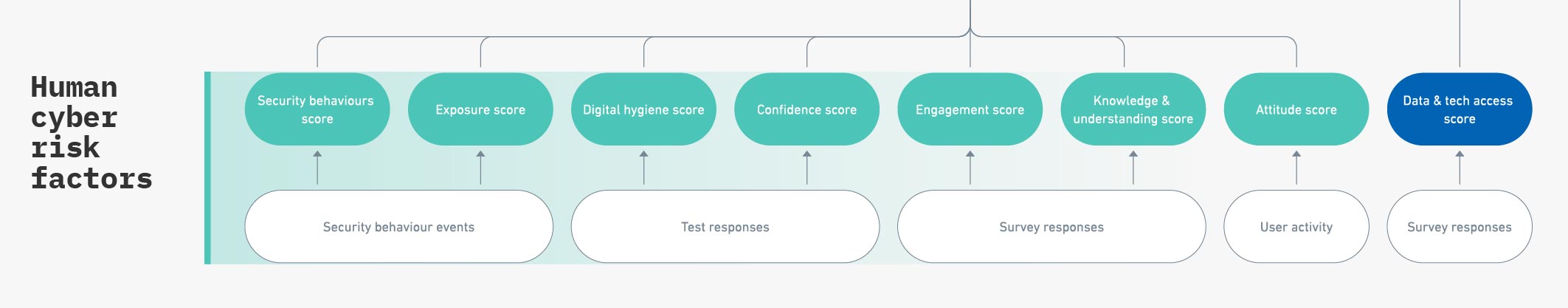
Image: Human cyber risk factors
FREE WEBINAR JUNE 12th /16:00 BST • 11:00 ET
Maturing SA&T
programs to Human Risk
Management strategies
Part 2: We’ve set the scene.
Time to dig into the report.
It’s time to get into the main messages of Forrester’s report. And we’ll weigh in with our unique CybSafe take too.
Take note: the full report is a) eye-opening, b) readable, and c) well worth your time. So look out for the download link at the end of this blog
PART 2
We’ve set the scene. Time to dig into the report.
1. Behavior change, not training completion
Forrester’s report paints a warts-and-all picture of the current state of security awareness training, where the role of humans in cybersecurity, including the risks they pose and are exposed to, is serious but under-discussed and misunderstood.
The report reveals a disconnect between training activity and actual security outcomes, concluding that the era of training people to tick boxes of outmoded and confusing compliance requirements is drawing to a close.
Despite increased training and testing, Forrester predicts that “90% of data breaches in 2024 will have a human element, up from 74% in 2023.”
The report argues that traditional SA&T often focuses on compliance checklists and generic training modules to meet a confusing web of outdated standards and regulations that mandated SA&T. They point out how these one-size-fits-all approaches fail to address the unique risk profiles of different users or departments.
As a result, people often go through the motions of completing training without actually retaining the information or changing their behavior.
And to confuse matters, recent attempts to revamp SA&T with “games, simulations, and quizzes.” But Forrester emphasizes how all of that training and quizzing failed to address the key issue of why companies are doing the training in the first place.
We agree with Forrester’s take. Traditional SA&T often fails to address the human element of cybersecurity. People are complex. So are the factors that influence their security behaviors.
Compliance-driven training doesn’t account for these nuances, meaning it ultimately falls short in changing user behavior.
HRM offers a more effective alternative by focusing on data-driven insights and personalized interventions. By identifying and targeting specific vulnerabilities, HRM programs benefit people and organizations by offering a more engaging and impactful experience.
PART 2
We’ve set the scene. Time to dig into the report.
2. Risk metrics, not activity metrics
Many organizations measure the success of their programs based on training completion rates or simulated phishing clicks.
Forrester says that these metrics don’t tell the whole story.
Because they don’t.
The report emphasizes the importance of measuring risk outcomes, instead of training activity. It points out that HRM solutions manage and reduce cybersecurity risks posed by and to humans by detecting and measuring human security behaviors and quantifying human risk.
In other words, effective HRM goes beyond simply delivering training and focuses on measuring outcomes, i.e. whether that training actually translates into a reduction in risky behaviors and security incidents.
Again, CybSafe is on the same page. Measuring risk outcomes is crucial for a successful HRM program.
By tracking the impact of your interventions on user behavior and security incidents, you can continuously refine your approach—and reach for maximum impact.
HRM’s data-driven approach propels your program beyond a “check-the-box” mentality. It shifts the focus towards achieving real-world security improvements. By doing so, it allows you to prioritize resources and tailor your interventions to address the most pressing security risks.
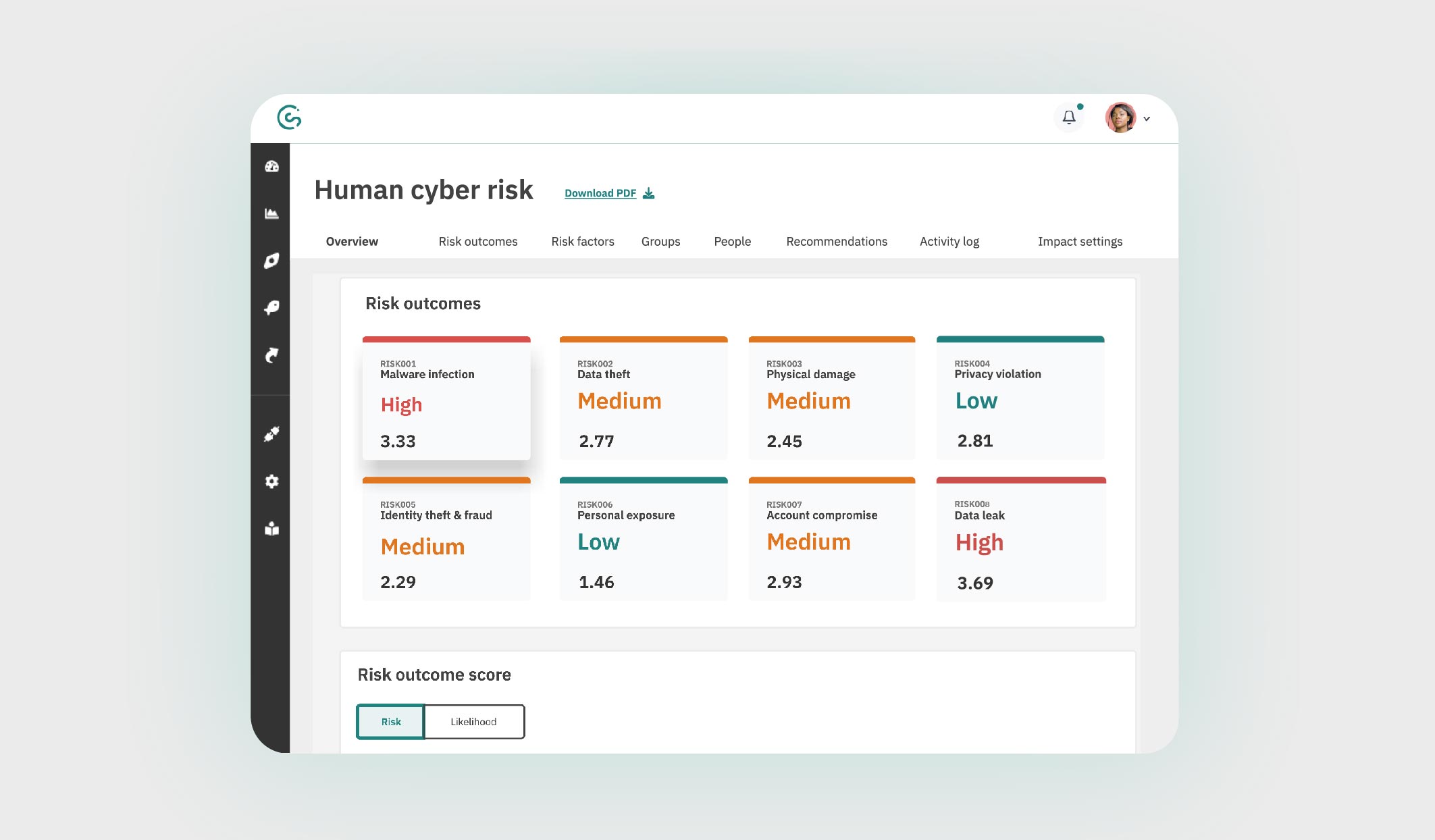
Image: The CybSafe human cyber risk dashboard. An industry first.
PART 2
We’ve set the scene. Time to dig into the report.
3. Personalized interventions, not generic controls
Data is the beating heart of a successful HRM program, says Forrester.
The report describes HRM as “an evidence-based method to train people and initiate policy interventions based on their risk profile.”
They set out that analyzing user behavior, security incidents, and other relevant data points is how organizations can shed light on their unique human risk profile. This data can then be used to personalize training interventions, prioritize mitigation strategies, and measure the effectiveness of your overall security posture.
What Forrester is highlighting here is that Effective HRM requires a deep understanding of your human risk landscape. This is a view we share.
Data is a key ingredient in unlocking the raw potential of HRM. By leveraging data analytics, organizations can identify the most common security risks associated with specific user groups or departments.
This allows for targeted training and interventions that address the specific vulnerabilities of each population. For example, employees who frequently access sensitive data may require more in-depth training on phishing scams compared to those with limited access. Data-driven HRM empowers organizations to make informed decisions about where to allocate resources and ensures that security awareness programs are truly relevant and impactful.
PART 2
We’ve set the scene. Time to dig into the report.
4. Science, not snake oil
Forrester recognizes the challenges that come with an emerging paradigm shift…
Hype.
As HRM’s star rises, so does the buzz. And vendors will naturally want to capitalize on that buzz.
As Forrester puts it:
“Exploiting the hype, some vendors have simply rebranded their computer-based training offerings as HRM without the data-driven behavioral identification and response capabilities.”
Forrester is right. It’s common for vendors to follow the hype, and for their marketing departments to write checks that their platform can’t cash.
It’s good (and necessary) that HRM is gaining momentum. But careful vendor selection is paramount.
If you’re looking for a simple litmus test to determine if a vendor is able to support a human risk management program, ask them this…
How many security behaviors do you measure and influence using objective data?
We could write thousands of words on vendor selection alone. We won’t do it here, though. What we will do is tell you what a solid HRM approach offer looks like. Or, rather, what CybSafe’s unique HRM approach is all about.
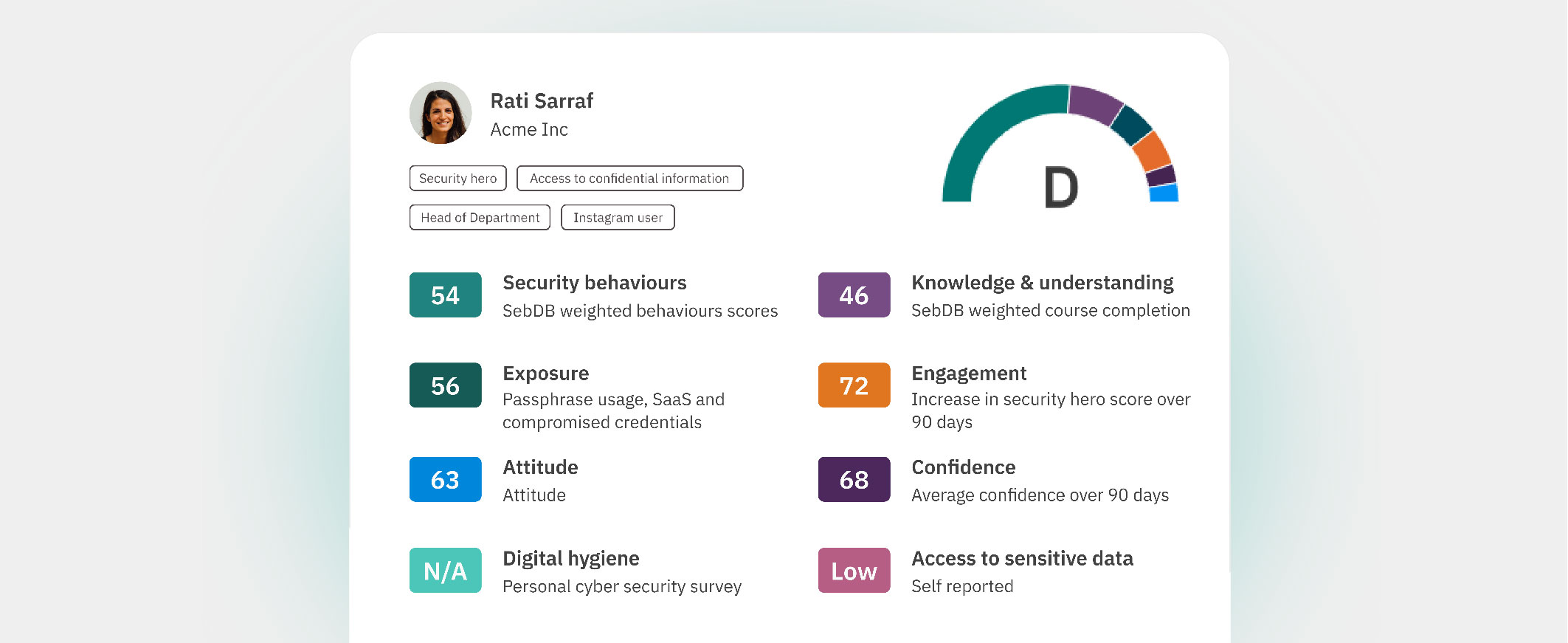
Image: A CybSafe scorecard showing an individual’s progress based on contributing human cyber risk factors.
Part 3: What makes CybSafe’s approach to HRM unique?
We pride ourselves on the fact that we’re the only organization with a commercially funded Science & Research team focused exclusively on the study of human risk management and human factors in cybersecurity.
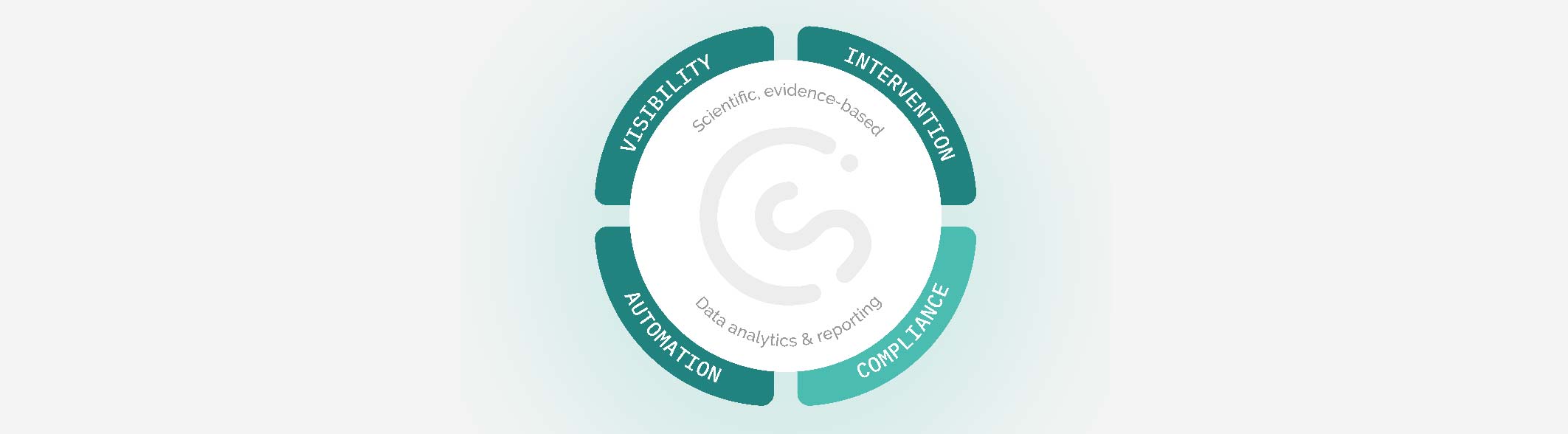
The CybSafe HRM platform helps organizations more effectively adopt HRM by helping them in 4 main areas:
-
- Visibility
- Interventions
- Automation
- Compliance
As the diagram suggests, all of this is bound together by evidence-based scientific research, and data analytics and reporting.
Aas already mentioned, central to HRM is a focus on security behaviors. As a result, everything in the CybSafe platform is underpinned by SebDB, the world’s security behavior database.
CybSafe’s HRM reporting is therefore easily correlated to the impact on risk outcomes. Not activity. Impact
It also makes it easy for organizations to measure and report on the full range of human risk factors.
PART 3
What makes CybSafe’s approach to HRM unique?
Conclusion
Forrester’s report has officially thrown down the gauntlet: compliance-driven SA&T is ineffective. Officially.
A fit-for-purpose security posture is contingent on a critical shift: moving beyond the “check-the-box” mentality of traditional SA&T, and towards a more data-driven and outcome-oriented approach.
Evidence-based HRM will have a positive influence on employee security behavior and help instill a security consciousness.
HRM is an approach that requires organizations to use behavior data to determine the impact of their risk management efforts.
Organizations that have adopted HRM also have the added benefit of being able to use the same behavior data to initiate and automate adaptive policies and interventions that protect employees and the organization from cyber incidents.
And for those at the start of the journey, selecting the right HRM partner is both a sizable challenge, and an absolute must.
Get the full picture: Download the Forrester report now.
Available to Forrester subscribers or for purchase.
PART 3
What makes CybSafe’s approach to HRM unique?
Is my organization ready for CybSafe?
No one wakes up and just “does” human risk management. It’s a journey.
Many prospective CybSafe customers only need to achieve SA&T compliance, increase engagement, and reduce phishing & ransomware risk.
They’re pleasantly surprised to learn CybSafe does these things, and starts them on the HRM path, and does it for the same cost as their traditional SA&T provider.
GUIDE educates and engages people—while helping achieve compliance.
Customizable, and designed with the modern, remote and hybrid working environments in mind, GUIDE is the perfect start to any human risk management strategy, for any organization.
PHISH simulates modern-day threats, and supports people in lowering their phishing and ransomware risk.
To help address risk on all fronts, PHISH combines seamlessly with our other products, giving you a truly holistic approach to phishing and ransomware risk reduction.
And for those organizations who have begun their HRM journey, and are wanting to unlock the full power of their existing tech stack, we have this…
RESPOND leverages existing data, tooling, and behavior event intelligence for a wider view of risk.
RESPOND analyzes potential cybersecurity threats using existing security tools and data, nudges users, enrolls people into behavior-triggered workflows, and alerts security teams.
PART 3
What makes CybSafe’s approach to HRM unique?
What’s the unifying factor?
But don’t just take our word for it. We’re lucky enough to work with an awesome group of visionaries. All these organizations have seen a reduction in security incidents related to human error.
If you’re ready to experience it first hand, book a demo, and witness the transformation.
Here’s to blazing a trail.
CybSafe.