A cheat guide for security awareness professionals
If you’re a security awareness professional, or in the business of managing human risk, it’s important to understand the difference between risks, threats and vulnerabilities. It’s also important to understand the relationship between the three.
No ifs. No buts.
It’s simply not optional if you want to be credible within security, and effective at managing risk.
This understanding will make you more effective in your job, and it will allow you to discuss risks and security behaviors more confidently with your security teams – as a genuine human risk specialist.
What is “risk”?
Risk is the potential for damage/harm/loss. (2)
In the context of security it is “the potential for loss, damage, or destruction of assets or data caused by a cyber threat”.
Think about that.
Risk is not a thing.
It is the potential for a thing to occur.
OUR HOUSE
Let’s imagine that we’re thinking in terms of our house. Risk is the potential for a particular bad thing to happen to our house.

The level of risk your organization faces is often expressed as your “risk profile” (5).
Your organization’s risk profile fluctuates depending on internal and external factors. It incorporates not just the potential or probability of a negative event, but the impact that event may have on you.
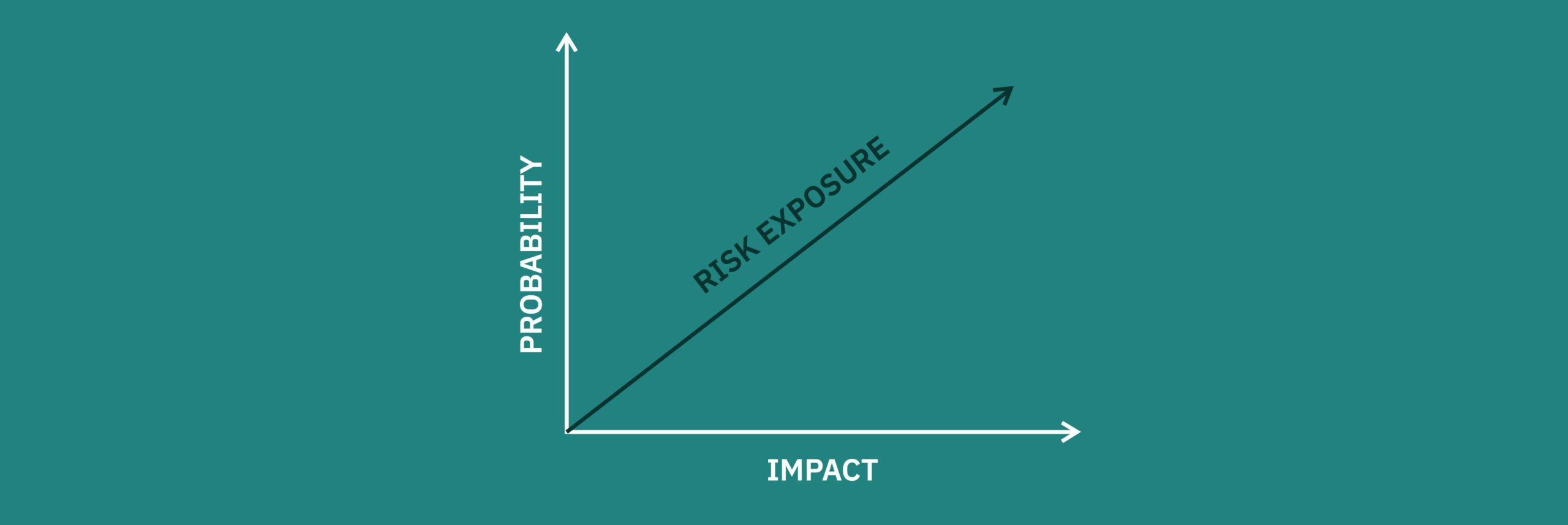
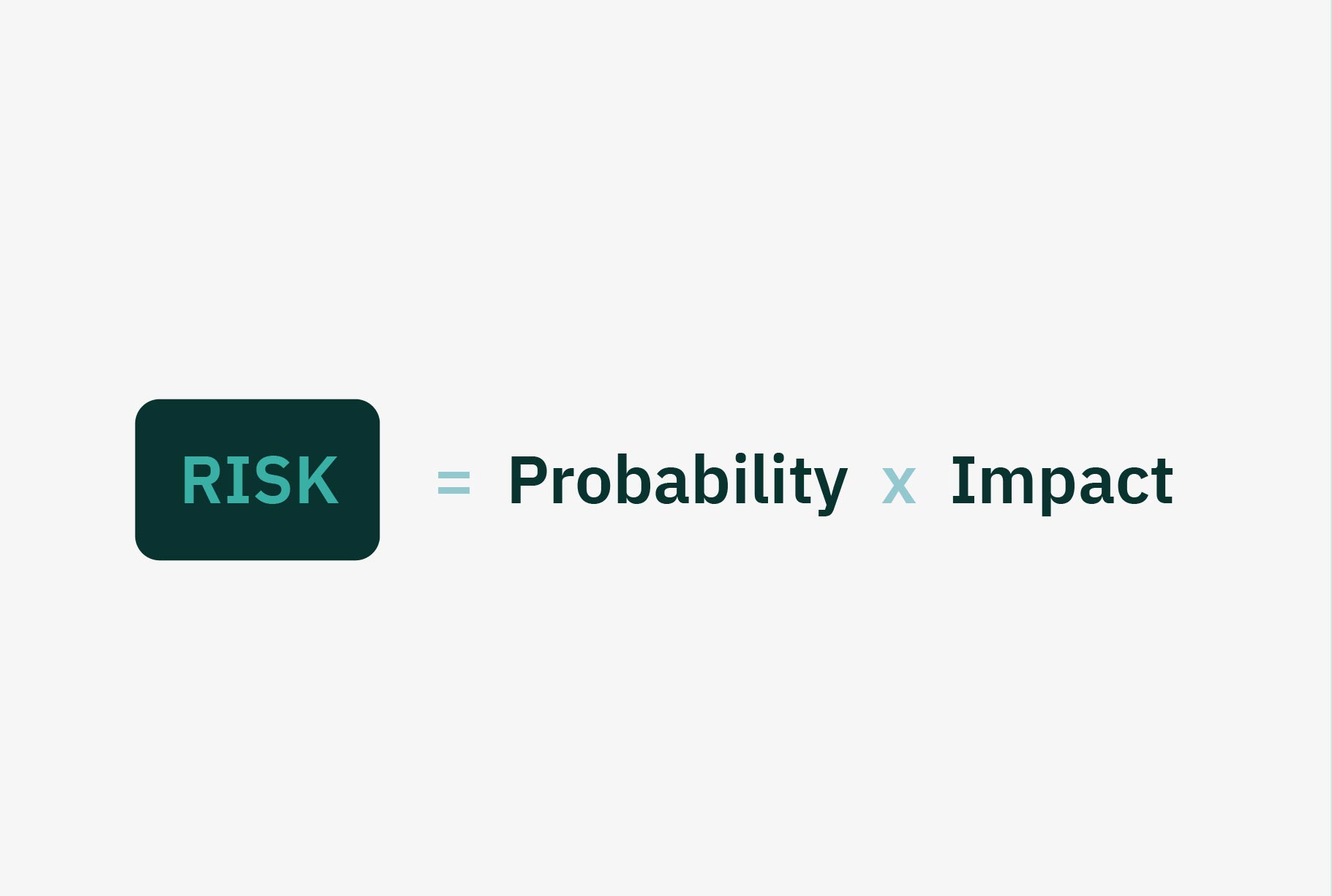
This is because in risk analysis, risk is traditionally considered a function of probability and impact.
The probability is the likelihood of an event occurring and the impact is the consequence. Put another way, it is the extent to which your organization is affected by an event. (6)
OUR HOUSE
Again in the context of our house, risk is a function of the probability that a specific bad thing happens (ie. how likely is it that this bad thing happens to our house?) …and the impact of that bad thing – (ie. just how bad would that bad thing be for us if it happened?
What is a “risk outcome”?
It’s important to be specific when talking about risks. It also makes everything much easier and much clearer.
When we say we are concerned about risk, we must be concerned about something in particular. This is known as a risk outcome.
I find it helps to use the phrase “TIART” when talking about risks. “(T)here (I)s (A) (R)isk (T)hat…”
A risk outcome is the specific something (damage, loss-like or harmful) we want to avoid. It’s the actual result if that risk actually occurred.
-
- “TIART… my house is burgled and all my property is stolen.”
- “TIART… we are victims of a cyber incident and out network suffers a severe malware infection (ie. ransomware or phishing)”
OUR HOUSE
So, in the context of our house, a risk outcome might be “having all our property stolen”. Another one might be “all our property being destroyed by water damage”.

What is a “vulnerability”?
Vulnerability is the weakness itself, that exposes you to threats, and therefore increases the likelihood of a negative event. (3)
Because of a vulnerability, there might be increased risk. But the vulnerability itself isn’t a risk.
OUR HOUSE
Again, in the context of our house, a vulnerability might be a window on the first floor that has been left open. Another vulnerability might be some tiles on the roof that haven’t been installed properly. Or another might be a key that has been mistakenly left in the back door.
These are vulnerabilities. But they are not risks. These vulnerabilities expose our house to threats, such as a threat agent gaining unauthorized access, and increase the chance of something bad happening to our house. But by themselves, they aren’t necessarily THE bad thing.

What is a “threat”?
A threat is anything that can exploit a vulnerability, intentionally or unintentionally and cause damage/harm or loss. (4)
Different organizations face different threats. For example, different threat actors pose different threats to different organizations.
Cyber criminals are threat actors. Hacktivists are threat actors. Nation state cyber attackers are threat actors. Script kiddies are threat actors. (7) And threat actors often exploit vulnerabilities.
OUR HOUSE
Again, back to our house, what might the threats be? Well anything that could exploit the vulnerability and cause damage, harm or loss. So, a threat might be a burglar. But another threat might be rain. And another threat might be a cat (having parties in your house whilst you’re away).

Where do user “security behaviors” fit in?
Inappropriate or suboptimal human (user) security behavior is a potential vulnerability in the context of your whole system. (Your ‘system’ is everything in the organization that works together to deliver the chosen output.) This is indisputable because threat actors often exploit inappropriate or suboptimal human (user) security behavior.
(Note: User security behavior is just one potential vulnerability. One of many. So none of this “weakest link” bollocks. That’s nonsensical. You have many links in your system. And many of them are neither weak nor strong. This language isn’t helpful when talking about human beings. Stop being lazy. If you mean “people are important because they are often the targets for cyber attackers”, then just say that.)
OUR HOUSE
In the context of our house, user behavior in security is just like a person’s behavior round the house. The person isn’t the vulnerability themselves. But the actions they take could introduce vulnerability.
- ”…Did they shut the window upstairs, or leave it open?”
- “…Did they lock the door?”
- “…When they locked the door, did they remember to take the key with them?”
- “…or did they leave the key in the door?”
- “…And when they laid the tiles on the roof did they do it properly?”

Remember, security behaviors aren’t all as important as each other. And their relative importance may change over time. So you need to know which security behaviors to prioritize and address.
Helpfully, all the security behaviors you might ever need to consider are probably laid out for you in the Security Behavior Database, or SebDB.
So, if the thing we’re concerned with is our property being destroyed by water damage (the risk outcome) then a key mistakenly being left in the lock (the vulnerability) probably isn’t too much of a concern. Likewise, if we’re worried about all our stuff being stolen (a different risk outcome), then badly laid roof tiles (the vulnerability) don’t create much risk.
Security behavior is also what is known as a behavioral risk factor (1). But it is not the risk itself.
So…how do you know which security behaviors (vulnerabilities) to focus on? Well, that’s where being clear about risk outcomes is extremely helpful.
Remember a security risk outcome is the result if a security risk actually occurs. These are the things that most organizations and security teams are keen to avoid.
Some examples of security risk outcomes include:
If you think about it, the likelihood of these risk outcomes occurring is based on a variety of risk factors. User security behaviors are just one of the risk factors. But they are a really, really important factor.
Also, different security behaviors have different levels of impact on the different risk outcomes.
OUR HOUSE
Remember our house analogy…🏠
The risk outcomes are things like “having all our property stolen”. Or having “all our property destroyed by water damage”.
The likelihood of these risk outcomes occurring is based on a variety of risk factors.
The occupant’s actions are just one of the risk factors: The open upstairs window, key left in the back door, or dodgy roof tiles.
But there are others: proximity to a criminal lair, weather forecast, amount of police patrolling the neighborhood etc.
So, what is human risk management (HRM)?
Understanding risk sits at the heart of human risk management.
You can’t manage risk if you don’t understand what risk is. No one will take you seriously. And nor should they.
Not all risk is equal, and management of risk requires prioritization. Some risk will be acceptable. Some won’t. The process by which we categorize risk, and the steps we take to mitigate it is human risk management. In order to understand HRM we need to understand human cyber risk.
Human cyber risk is the extent to which an organization is exposed to loss or harm because of their people’s security attitudes, situational awareness, knowledge, decisions, and behaviors.
You can learn more about human risk management in our definitive guide here.
The bottom line
As a security awareness or human risk management professional a good understanding of the difference between risks, threats and vulnerabilities will help you better manage the human aspect of cyber security.
You will also be able to help your security team make better risk decisions.
You will also be more credible in the eyes of your leadership and your security peers.
You will be considered more than “just” an educator, or a communicator.
A focus on risk helps you clearly articulate the importance of security behaviors. These are the vulnerabilities you need to address.
It also helps you begin to understand the breadth of human risk management.
Final word
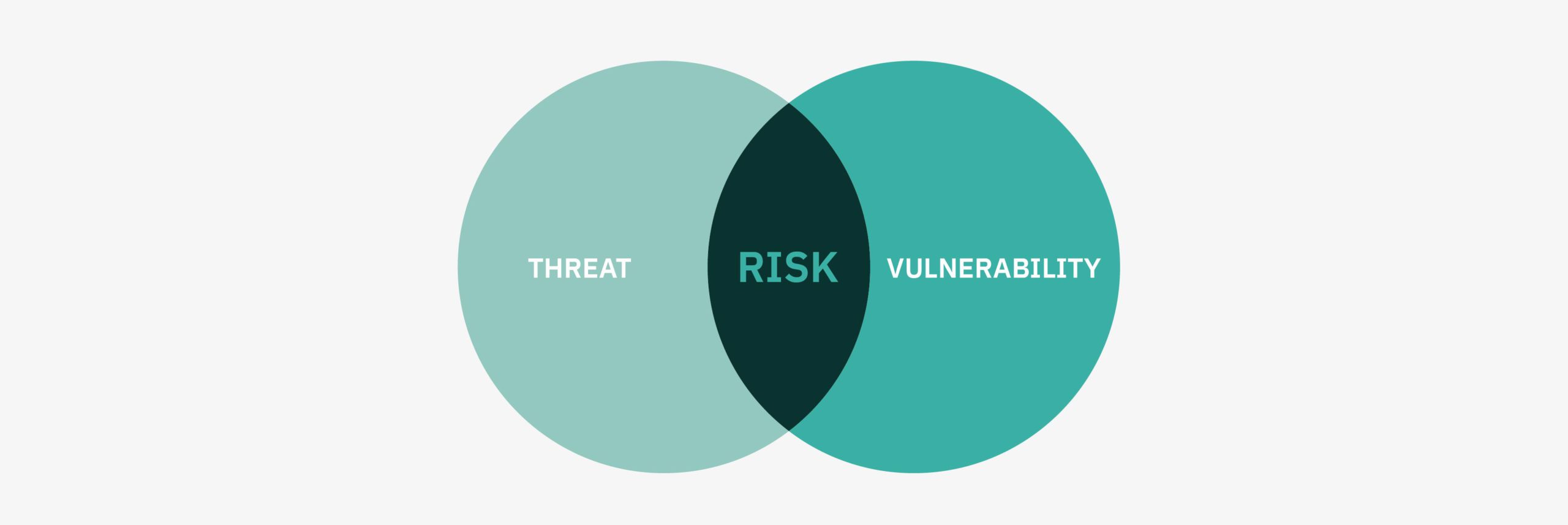
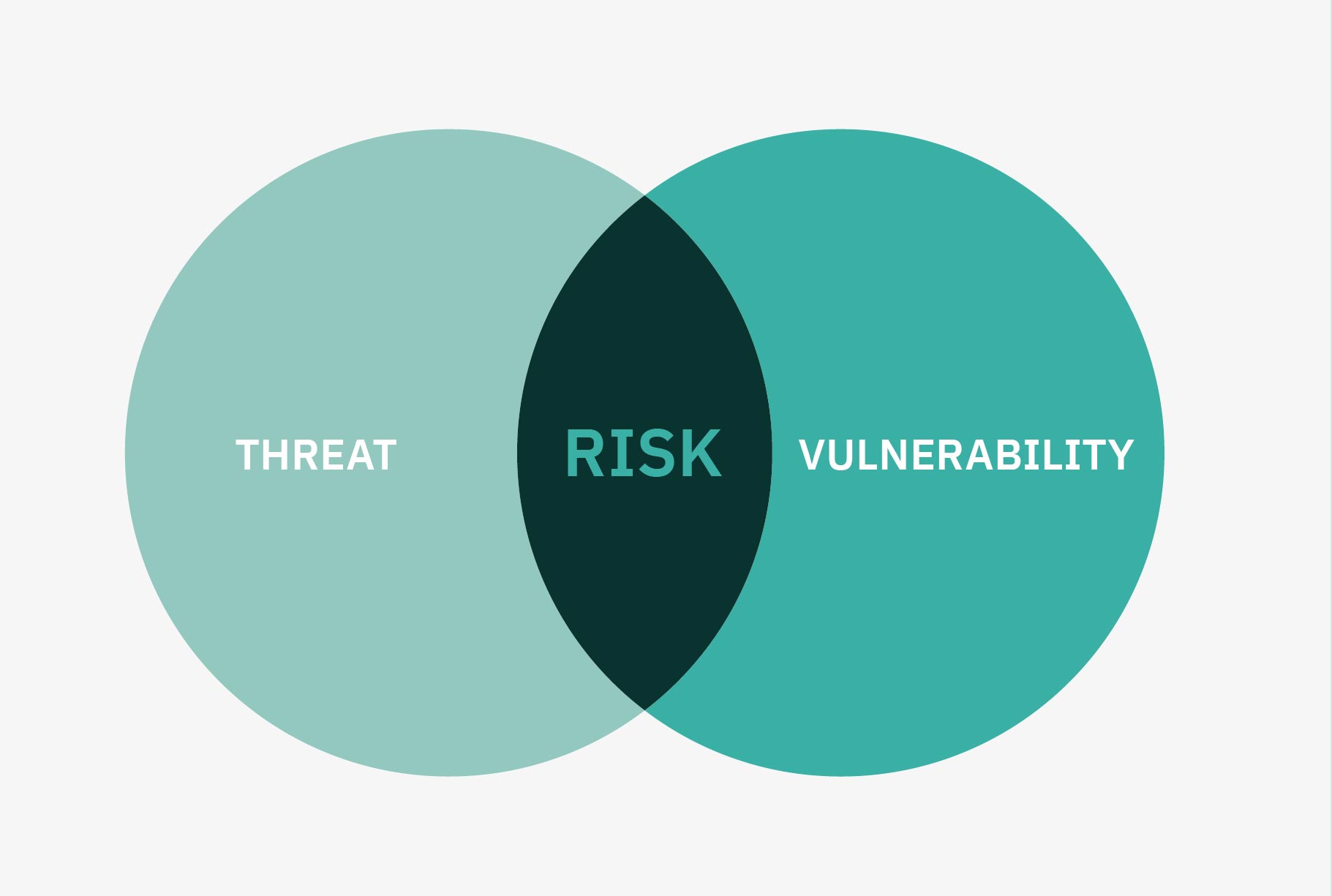
If you truly understand risk you’ll understand that it’s found at the intersection of ‘vulnerability’ and ‘threat’.
Your employees aren’t a risk. They can’t be. You might consider some things they do (behavior) as introducing vulnerability to your system. But a vulnerability in and of itself is not a risk. A vulnerability might mean increased risk. But not necessarily.
In extremis, you might consider them a threat (hence insider threat as well as insider risk programmes). But threats aren’t risks. Threats might mean increased risk. But not necessarily. And anyway, the vast majority of your people are not a threat.
The concept of risk really isn’t that complicated. It’s just not well-understood by most of the people who use the word.
Hopefully now when you use the words risk, threat and vulnerability, it is.
References
(1) https://www.sciencedirect.com/topics/medicine-and-dentistry/behavioral-risk-factor
(2) https://www.kennasecurity.com/blog/risk-vs-threat-vs-vulnerability/
(3) https://www.kennasecurity.com/blog/risk-vs-threat-vs-vulnerability/
(4) https://www.digiaware.com/2018/12/vulnerability-threat-risk-key-difference-examples/
(5) https://www.techtarget.com/searchsecurity/definition/risk-profile
(6) https://www.cio.com/article/238969/risk-likelihood-x-impact.html
(7) https://www.digitalhands.com/guides/cybersecurity-threat-actors