Are security awareness gamification and personalization gimmicks or genius?
Did you know Velcro was once considered completely pointless? And that people thought WiFi would never catch on?
First impressions can be wrong. Spectacularly so.
Take cybersecurity personalization for instance. It’s got just as much potential. But plenty of people don’t see it. Not yet anyway.
Likewise, fun, novelty and competition are so often dismissed, yet they can help make the most of personalization.
Personalization x fun = powerful!
Put down that box of poorly made “I 💘 cybersecurity” t-shirts! Humor us, and read on.
Because recent research revealed how personalization is the secret sauce that brings significant increase in positive security actions. It’s called Cyber Security Quirks, and it’s a definite eye-opener.

Personalised interventions
for Human Cyber Resilience
Oh, and if you want an overview on the role of personalization in cybersecurity? Our essential guide will get you up to speed.
Right, so, back to it. Where were we?
The future of cybersecurity is all about harnessing the power of the personal. But we can’t just slap someone’s first name on generic messages.
We need to use things that work. Things like fun! And novelty! And a dash of friendly competition.
Because let’s face it, Ryan in your comms team isn’t going to be engaged by a security lecture that drones on about phishing attacks. (Well, he might engage in some nodding off.) But an interactive quiz that exposes Ryan’s own specific social media vulnerabilities? It’s exactly the wake-up call he needs.
Fun and novelty matter. To Ryan, and to every single person in your organization. Yes, fun and novelty also attracts labels—labels like “gimmick”—but here’s the thing.
We need to stop dismissing gimmicks
We need to ditch the skepticism about so-called “gimmicky” personalization tactics. Seriously.
Because in the right hands, they can be powerful tools for positive change.
They can make security awareness relevant, engaging…even (gasp) fun.
So let’s take a look at three popular personalized cybersecurity “gimmicks”. Their potential impact, tips on how to use them, and the verdict on their potential.
Let’s do this!
Making security stick:
Unpacking the top tricks for interactive learning
The Cyber Security Quirks report highlights three potential avenues for personalized cybersecurity interventions: password quizzes, escape rooms, and password strength meters. Let’s take a look.
Password quizzes
Essentially, guided password creation practice, AKA an exercise in self-discovery. Password quizzes prompt people to think about their current password strength strategies without using fear tactics…and almost without people noticing they’re doing it.
For example, in the Quirks report research, we asked detailed questions, such as ‘Does your password include names of your family members or pets?’ and ‘Does your password include references to your or your family member’s birthday?’. This prompted people to think about their insecure password practices.
And as any of us who’s dabbled in pop psychology knows, contemplation is an important early step in making changes.
How to personalize: Opt for insightful questions, targeted feedback, and playful gamification to spark contemplation and empower lasting change.
The verdict: Very useful, but with caveats. Asking thought-provoking questions like those in your study can nudge people towards introspection and self-improvement. However, overreliance on quizzes without follow-through can breed apathy. Consider integrating them with actionable feedback, personalized training modules, and even playful gamification to sustain engagement and drive lasting change.
Escape rooms
A cybersecurity escape room teaches people about cybersecurity risks and best practices in an immersive, fun way.
Scenarios often involve simulated cyberattacks or security vulnerabilities, bringing common threats to life.
Participants have to collaborate, problem-solve, and apply their cybersecurity knowledge to overcome the challenges and “escape” the scenario within a set time.
How to personalize: Contextualize risk information to different groups and grade the advice based on their level of cyber security skills.
The verdict: Engaging, but potentially resource-intensive. Immersive escape rooms offer a fun and collaborative way to learn essential security concepts, but their scalability and cost-effectiveness might prove hurdles for some organizations. Consider smaller-scale simulations targeted at specific risk groups for wider reach.
Password strength meters
This is a simple way for people to practice their password creation and receive immediate feedback.
For example, it could include information on how long the password would take to hack and enhance people’s confidence and ability.
And as a bonus, it fosters some healthy competition as people jostle for the accolade of least hackable password.
How to personalize: Let people customize their password rules to fit their needs and comfort level with risk. This way, they’re in charge of their own security.
The verdict: Useful, but context matters. Immediate feedback on password strength can boost confidence and encourage stronger choices. However, relying solely on meters can create a false sense of security if not paired with education about different attack vectors and password hygiene practices. Personalized rules and contextual risk information for varying user groups can add valuable nuance.
Gently does it
It bears repeating here. Cybersecurity’s inevitably a heavy topic…but the delivery needn’t be.
Remember, the secret super power of the cybersecurity gimmick is that nobody takes them overly seriously.
And that’s what’s so great about them!
They can serve as a light and gentle approach to engage people.
So, even if you don’t opt for escape rooms or password-ometers, keep interventions approachable. That way, people are far more likely to embrace and internalize the lessons.
And be consistent
It’s not just about the specific activities. Every interaction users have with cybersecurity interventions plays a crucial role.
From the platform design to messaging, personalization should be seamlessly integrated.
Subtle cues and tailored content, like the ones in the Cyber Security Quirks report, can significantly influence user behavior and decision-making.
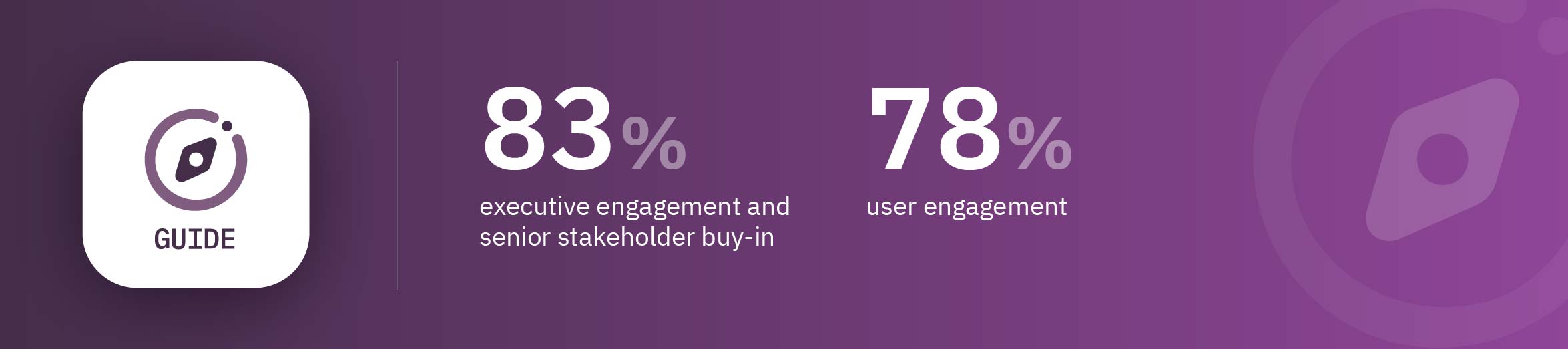
How CybSafe does it
CybSafe’s GUIDE, PHISH, and RESPOND are all designed to turn routine activities into engaging experiences.
- Smart learning paths: Tailors learning based on strengths and weaknesses.
- Micro-learning nudges: Delivers quick reminders within daily workflows.
- AI-powered coaching: Provides personalized feedback for a dynamic learning environment.
- Tailored phishing simulations: Customizes simulations for a realistic and engaging experience.
- Detailed vulnerability reports: Generates reports highlighting vulnerabilities for targeted training.
- Gamified learning: Interactive simulations and personalized dashboards make learning enjoyable.
- Personalized dashboards: Tracks progress and encourages healthy competition.
- Automated prompts: Triggers personalized prompts based on user behavior.
- Tailored playbooks: Allows creation of personalized playbooks for engaging and relevant security guidance.
Alright, let’s wrap it up
In the high-stakes game of cybersecurity, all proven tactics deserve a seat at the table.
That means personalization and gamification deserve a seat at your table.
They push interventions beyond generic one-size-fits-all approaches, and help you craft experiences that resonate with people.
When you do that, good cybersecurity habits stick…like Velcro.
Download the full report for more about personalization interventions—like the 3 key factors that drive every action anyone takes, ever!