
Data Theft
Data theft is the intentional stealing of data.
Behaviours

SB013: Reports known or suspected security incidents
Reporting known or suspected security incidents helps protect people as well as their place of work. If the ...
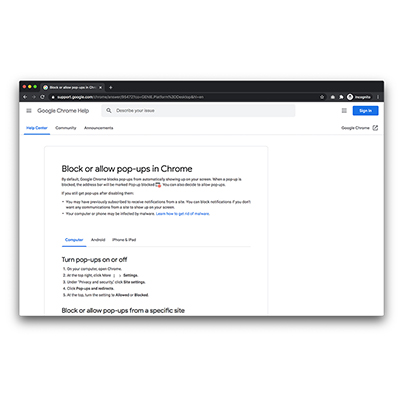
SB017: Blocks browser pop-ups
Most web browsers come with a range of security options. One option is to automatically block pop-ups. Enabling ...

SB023: Enables firewalls on all compatible devices
A firewall is a set of virtual rules that help prevent malicious applications from communicating with a device. ...

SB023a: Enables firewalls on all compatible workplace devices
A firewall is a set of virtual rules that help prevent malicious applications from communicating with a device. ...

SB024: Enables auto-updates for workplace devices (if permitted)
Software updates reduce exposure to known security vulnerabilities. Most devices can be set to auto-update when ...
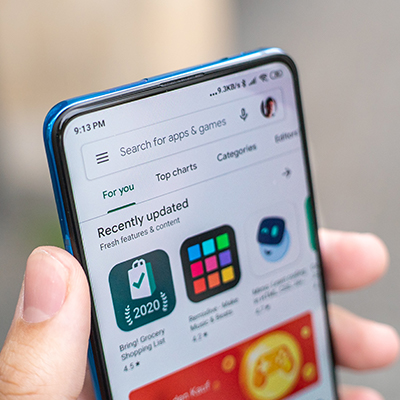
SB025: Enables Google Play Protect (Android devices only)
Google Play Protect should be enabled on all Android devices. With Google Play Protect enabled, apps downloaded ...

SB025a: Enables Google Play Protect on all workplace devices (Android devices only)
Google Play Protect should be enabled on all workplace Android devices. With Google Play Protect enabled, apps ...

SB025b: Enables Google Play Protect on all personal devices (Android devices only)
Google Play Protect should be enabled on all personal Android devices. With Google Play Protect enabled, apps ...

SB026: Restricts the number of users with administrator privileges, and uses the administrator accounts only where necessary
User accounts have fewer privileges than administrator accounts. User accounts deny malware escalated permissions. ...

SB031: Runs anti-virus scan if a new, unexpected icon or pop-up appears on the desktop
Unexpected icons or pop-ups on a computer’s desktop can indicate malware. Running an antivirus scan can help ...

SB032: Does not insert unauthorised devices/media into work devices/network
Malicious USB (or other plug-in) devices can be used in cyber attacks. They can be used to upload malware, steal ...

SB035: Changes default passwords (if possible) on all internet-connected devices
Internet-connected or “smart” devices are often protected with default passwords. Many of these passwords ...

SB036: Secures devices with automatic screen locks
Devices can be protected with screenlocks (like pins, patterns and passwords). This can help prevent unauthorised ...

SB036a: Secures mobile devices with automatic screen locks
Mobile devices (e.g. phones and tablets) can be protected with screenlocks (like pins, patterns and passwords). ...

SB036b: Secures laptop and desktop devices with automatic screen locks
Laptops and desktops can be protected with screenlocks (like pins, patterns and passwords). This can help prevent ...

SB037: Locks devices when they're not in use
Locking devices when not in use prevents unauthorised access. This is especially important in common areas, such ...

SB037a: Locks mobile devices when they're not in use
Locking mobile devices when not in use prevents unauthorised access. This is especially important in common areas, ...

SB037b: Locks laptop or desktop device when not in use
Locking laptops and desktops when not in use prevents unauthorised access. This is especially important in common ...

SB038: Shuts down devices when not in use
Shutting down a device when not in use ensures a second password is required to access it.

SB039: Turns off Bluetooth when mobile device not in use
Bluetooth can be used to access devices. Turning Bluetooth off when not in use conserves battery and improves ...

SB040: Uses a virtual private network (VPN) on mobile devices
A VPN encrypts the data sent to and from devices over the internet, preventing it being read in transit. They ...

SB041: Enables a VPN when using public Wi-Fi
Data sent over a public Wi-Fi network is at greater risk of being intercepted. A Virtual Private Network (or VPN) ...

SB042: Uses tethered mobile device to avoid using insecure Wi-FI
Tethering to a mobile device is more secure than using public Wi-Fi without a VPN. 3G and 4G connections are both ...

SB043: Disables "automatically connect to Wi-Fi" on mobile devices
Allowing devices to automatically connect to public Wi-Fi increases the chance of data being intercepted.

SB044: Enables encryption
Encrypting a device prevents the data on the device from being accessed should the device be lost or stolen. Some ...

SB046: Securely removes data from devices before decommissioning
Data should be securely removed from all devices (e.g. laptops and mobile phones) before they are decommissioned. ...
SB049: Covers webcam when not in use
Devices that have been compromised can have their webcams accessed. To limit further breaches to privacy and data, ...

SB063: Checks security credentials of unknown persons at work
Individuals should check the security credentials of unknown people they come into contact with in the workplace. ...

SB064: Prevents tailgating at security checkpoints
When passing through security checkpoints, people should check they are not being followed by others who do not ...

SB065: Does not share security passes or access tokens
Sharing security passes even with "trusted" contacts creates risk. People should only ever use security passes ...

SB066: Escorts visitors to ensure they follow security policies
Visitors should be escorted according to organisational policies. This reduces the risk of unauthorised access to ...

SB069: Reports lost or stolen devices to IT or Security team
Lost or stolen devices should be reported immediately. This allows the device to be locked or remotely wiped to ...
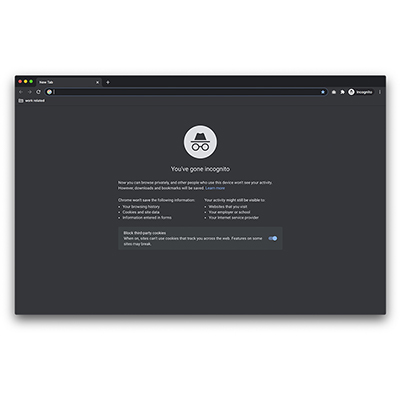
SB074: Uses a private browsing on shared devices
If workplace devices are shared between colleagues, private browsing should be enabled by default. This means ...

SB080: Verifies caller details from unexpected calls
Criminals sometimes use phone calls to try and elicit sensitive information from people. This is called 'Vishing'. ...

SB081: Checks instant messages for signs of deception
Criminals will often use instant messaging (e.g. Whatsapp, Facebook and Slack) as an attack vector. Unexpected ...

SB082: Uses known contact details to verify suspicious messages
Contact details can be spoofed. Receiving a message that breaks any norms should be met with suspicion. Using ...

SB083: Checks before “blindly” forwarding messages to workplace contacts
Messages from workplace contacts are more likely to be trusted than messages from other sources. Forwarding ...

SB087: Reports suspicious messages (e-mails, texts, phone calls)
Suspicious messages received via email, text or phone should be reported to a single point of contact. This allows ...

SB088: Checks emails for signs of deception
Criminals will often use emails as an attack vector. Unexpected emails should always be checked for malicious ...

SB089: Does not share MFA codes
Doesn't share MFA codes (including verfication codes and OTPs) with other people, preventing them from accessing ...

SB091: Does not forward work information to personal email addresses
Does not forward any work-related emails to their personal email addresses. This ensures that sentisive ...

SB092: Returns allocated devices when no longer needed
Returns allocated office equipment when no longer needed. This prevents idle devices from going into the wrong ...

SB094: Does not use personal devices for work unless authorised to do so
Has separate work and personal devices. Only uses personal devices for work if authorised by the employer, using ...

SB095: Does not share film recordings or photos from work locations
Sharing photos, videos or posting descriptive information about your workplace through your personal online ...

SB096: Does not carry sensitive work information or unauthorised devices to countries with high security risks
Does not carry sensitive work information or unauthorised devices to countries with high secuirty risks. Carrying ...

SB100: Takes additional measures to prevent eavesdropping when working outside the office
Ensures smart devices are turned off or not in the vicinity when discussing sensitive workplace information.

SB105: Uses a security key
Security keys are USB keys or dongles that work as an advanced form of multi-factor authentication. Using them ...

SB151: Does not use weak passwords
Using a weak password puts an account at risk of data breaches, takeovers, and various cyberattacks. Some sites ...

SB156: Discloses credentials to a phishing site
Disclosing credentials to a phishing site places the individual and their organisation at risk of account ...

SB156a: Discloses credentials to a simulated phishing site
Disclosing credentials to a phishing site places the individual and their organisation at risk of account ...

SB159: Does not click a phishing link
Clicking on a phishing link could lead you to a fake website that asks for private credentials, or tricks you into ...

SB161: Reports a suspected phishing email
Reporting phishing emails notifies IT or security teams that employees are being targeted by cyber attackers. ...

SB161b: Reports a simulated phishing email
Reporting phishing emails notifies IT or security teams that employees are being targeted by cyber attackers. ...

SB163: Does not open a phishing email
Some phishing emails include macros that autorun on opening. Even though these cases are rare, if possible it is ...

SB163a: Does not open a simulated phishing email
Opening a simulated phishing email informs the IT or security team that employees might be at risk of taking ...

SB164: Does not open an attachment in a phishing email
Opening attachments on phishing emails could lead to malware infections and cyberattacks.

SB164a: Does not open an attachment in a simulated phishing email
Opening an attachement in a simulated phishing email informs the IT or security team that employees might be at ...

SB177: Does not lose device through theft or negligence
Losing devices containing sensitive information through theft or negligence increases the likelihood of cyber ...

SB177a: Does not lose mobile device through theft or negligence
Losing a mobile phone or tablet containing sensitive information through theft or negligence increases the ...

SB177b: Does not lose laptop/desktop through theft or negligence
Losing laptops/desktops containing sensitive information through theft or negligence increases the likelihood of ...

SB182: Does not send sensitive information out of the business (email or otherwise)
Sending sensitive information out of business increases the risk that it might fall into the hands of people not ...

SB183: Does not send emails to unintended recipient(s)
Sending emails to the incorrect recipient increases the chance of sensitive company or personal information being ...

SB184: Does not share a file containing confidential information
Sharing files containing confidential information might increase the risk that unauthorised individuals see or ...

SB185: Does not post confidential information in a public messaging channel
Posting confidential information in a public messaging channel can be viewed by anyone and could be leaked ...

SB186: Does not post PII in a public channel
Posting Personally identifiable information (PII) in a public channel allows anyone to view the information and ...

SB187: Does not share a file containing PII
Sharing files containing Personally identifiable information (PII) could expose PII to someone other than the ...

SB188: Does not share sensitive information with unauthorised recipients
Sharing sensitive information with unauthorised recipients is harmful for the company and places the integrity of ...

SB189: Does not use unapproved applications on work devices
Using unapproved applications on devices may be harmful. They could cause your device to run slower, introduce ...

SB198: Does not use unapproved device for work purposes
Using unapproved devices for work purposes increases security risks. This could be for a variety of reasons ...

SB198a: Does not use unapproved mobile device for work purposes
Using unapproved mobile devices for work purposes increases security risks. This could be for a variety of reasons ...

SB202: Stores documents appropriately for their level of sensitivity
Documents should be stored in a manner that is appropriate for their level of sensitivity. Organisations are ...

SB203: Uses biometrics to access online account
People can access devices and accounts with biometric information (e.g. a fingerprint or facial scan). The unique ...

SB204: Uses biometrics to access mobile device
People can access devices and accounts with biometric information (e.g. a fingerprint or facial scan). The unique ...
Case study
Opshare Talent Solutions
In 2018, three former employees of Opshore Talent Solutions, an Indian recruitment consultancy, were arrested for data theft.
While employed by the consultancy, the trio stole information from their employer’s client database. The employees then resigned and set up their own recruitment consultancy.
Opshore Talent Solutions became suspicious after losing clients to the former employees. They reported their suspicions, and an investigation led to the arrest of the three men. All pleaded guilty to the accusations.
Opshore did not monitor data transfers within their organisation, nor did they check whether resigned or former employees still had access to the company records. The company also allowed employees to use personal computers in the workplace, which gave employees access to confidential information via personal devices.
UnityPoint Health
In 2018, UnityPoint Health suffered the biggest US health data breach of the year following two phishing attacks.
Criminals posed as a trusted executive and emailed employees to trick them into providing login information. Later investigations showed the fraudsters were trying to divert payroll and vendor payments to their own accounts.
The scam compromised the details of 1.4 million UnityPoint patients. The data included names, addresses, medical data, treatment information, lab results, insurance information, payment details and Social Security numbers.
Victims sued UnityPoint. They agreed to a $2.8 million settlement payment.
Learning from such a costly mistake, representatives from the health system stressed the importance of preventative measures. These include resetting the passwords of compromised accounts, implementing cyber security awareness training for employees, and enabling multi-factor authentication.
Nintendo
In 2020, criminals gained access to 300,000 Nintendo Switch accounts after stealing people’s login IDs and passwords. The accounts stored personal information like birthdays and email addresses.
After hacking the Switch accounts, the fraudsters also gained access to victims’ Nintendo Network IDs. They then used stored payment information to make fraudulent purchases via Nintendo’s official online store.
At first, the attack affected 160,000 Switch users. The figure rose to 300,000 as time went on.
Nintendo refunded fraudulent purchases and disabled logins as part of the recovery operation. They advised victims to reset their passwords and to avoid storing personal and sensitive information in online accounts.