Human behavior is fascinating. Some people dedicate their lives to studying why we do what we do. We have a whole security team at CybSafe that live and breathe behavioral science! So why do people continue to behave in ways detrimental to their health, safety and wellbeing?
From the philosophers of Ancient Greece to modern-day podcasters, human behavior is a deeply studied subject. In this blog, we’ll be looking at cybersecurity. We’ll be trying to understand why people struggle to display positive cybersecurity behaviors and how you can change this.
Hint: It’s a four-letter word that is used in positive psychology and football…
“If you don’t know where you are going, you’ll end up someplace else” – Yogi Berra
When you think of January, lots of things come to mind. Cold weather, grey skies, short days and what feels like the longest month of the year. New Year’s Resolutions are also an essential part of the start of the year for many people.
According to the University of Scranton, a whopping 92 per cent of people who set New Year’s goals never actually achieve them. Why is it so damn hard to achieve our goals? The first hurdle we fall at is how we define goals.
How many times have you heard the following:
“My goal is to be more productive”
“I want to become healthier this year”
“I want to be better at saving money”
On the surface, these are all worthy goals. But when you take a closer look, these goals are vague at best. Let’s take a look at the first example. The word “productive” is relative and can mean many different things. Even if you have your own idea of what productive looks like, how can you measure it? Which areas of your life does it relate to?
A great resolution to this is thinking about the end, or the “destination”, of your goal and working backwards. So a productive person is likely someone who plans their days out and sticks to their plan. A more effective goal would be “I want to plan my weekly schedule every Sunday night and complete 80% or more of the tasks on my to-do list”.
Where there’s a will, there’s a way!
Now, back to cybersecurity. If you are an information security specialist, chances are you already have plenty of well-defined goals related to your cybersecurity strategy . That’s the easy part! It’s typically a case of marrying the needs of the business with security requirements.
You’re probably asking yourself: “How do you make sure that Jane from Accounting is completing software updates?” or something along those lines. Protecting employee and company sensitive data from cyber attackers and ensuring system’s integrity isn’t easy. Understanding how behavior change works is a productive place to start.
In practice, we set goals when we need to do something that hasn’t happened yet and isn’t likely to happen on its own . Goals are usually things we want but have difficulty achieving even when we know they are achievable. Otherwise, we wouldn’t need a goal in the first place! Engaging in behavior isn’t the hard part; it is new behavior that is challenging.
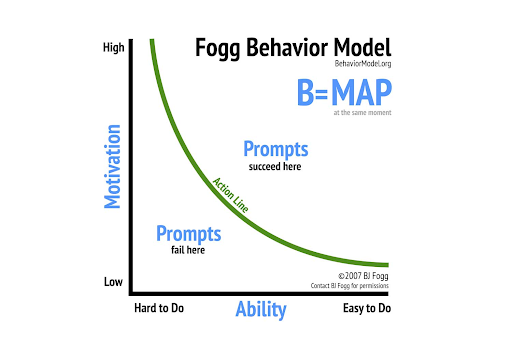
To understand why new behavior is so hard to do, it’s helpful to think about three dimensions that give rise to behaviors:
- Ability (or the “way” to do the behavior)
- Motivation (or the “will” to engage in the behavior)
- Prompt (or the “trigger” to do the action)
Behavior change can be neatly explained by Fogg’s Behavior Model:
Information alone doesn’t lead sustained behavior change. That’s why security awareness training isn’t enough for most people to avoid a cyber threat or attack. Seeing statistics and data won’t change someone’s behavior in the long term. Behavior happens when three things come together at the same time: motivation, ability and prompt ..
For security behavior to change, movement needs to happen across the axis past the “action line”.
You can use this framework as an effective tool for diagnosing the source of the difficulty.
Let’s look at an example; setting secure passphrases for key accounts to protect them from data breach. It’s fair to describe it as a simple and routine task as it requires low skill and low motivation. But why are people still not doing it? Is low motivation the reason why people can’t be bothered to use strong passphrases or adhere to company security policy? How can you increase motivation to encourage behavior change?
As a person’s motivation and ability to perform the desired behavior increase, the more likely it is is that they’ll do the behavior. There’s an inverse relationship between motivation and ability. The easier something is to do, the less motivation is needed to do it. On the other hand, the harder something is to do, the more motivation is needed.
If you want a behavior to take place, in your cybersecurity strategy look for ways to boost motivation or ability (or both). How can you boost these dimensions and move people above the action line? Cybersecurity goal-setting is a great place to start.
Are your goals S.M.A.R.T enough?
Goals play a dominant role in shaping how we see ourselves and others. They are even used as a psychological tool for increasing productivity. The S=M=A=R=T rule, coined by George T Doran, is a handy mnemonic that can make your goals more successful.
S is for Specific: Specific is the need to have a goal dedicated to specific behavior. Generic goals are less effective as they don’t address a particular set of problems.
M is for Measurable: To have a measurable security goal or strategy, you need to know you’ve accomplished the goal. You need to define metrics so you can measure and track achievement. Reducing the number of people that click on phishing links is an example of a measurable goal.
A is for Attainable: Everything is achievable in theory. But time, budget, resources and scope are factors that determine how attainable a goal is.
R is for Relevant: A security goal is relevant if it makes sense to be implemented and if it applies to your problem. You can’t secure everything and protect against every possible cyber threat. Choose the goals that matter to your organization and fit the other S.M.A.R.T attributes.
T is for Time-bound: In cybersecurity, we’re always confronted with time. If securing something takes too much time for people to do, it won’t get done. Time can also make a goal irrelevant. Setting deadlines is a way to overcome time constraints.
Setting SMART goals is essential, but only if people attempt to achieve them and feel motivated to do so. This is where effective communication of goals comes into play.
It’s all about how you say what you say
Communicating cybersecurity is not a new issue. People in the industry tend to frame cybersecurity as utopian or dystopian extremes. This can be counterproductive and result in inaction. Think of the famous line “Hell does not sell”. It feeds the idea that we are out of control and the problem can no longer be resolved.
This is where message framing comes in. It’s a useful strategy for communicating complex cybersecurity problems in a clear and accessible message. Goal setting is the antidote to this issue. Using goals is an effective way of framing a cybersecurity issue in a way that encourages action and fosters good cybersecurity practice. It also forces you, the goal-setter, to think of what the goal is, why it is critical and how to achieve it.
It’s a way of taking a problem that might not mean much to the average person and making it relevant to their day-to-day life in a very tangible way. It places the control in our hands reducing the risk of a security incident. Whether it’s using multi-factor authentication or reporting security incidents, goals give us a route to success against a cyber attack.
From goal setters to goal scorers
Behavior change is hard. Technology has the power to make it easier and more successful long term. To get people over the finish line, there are a few essential cybersecurity measures:
- Get some honest self-reporting: Ask people about their behaviors in a way that encourages transparency
- Set them a cybersecurity goals: By telling them exactly what they should achieve, people are clear on what they need to do.
- Explain why it is important: This is where you motivate them by explaining the benefits of the goal.
- Break the goal down into manageable steps: This increases their sense of self-efficacy and increases the likelihood of goal completion.
- Allow them to set reminders: By giving people the autonomy to choose when to do it, on their terms.
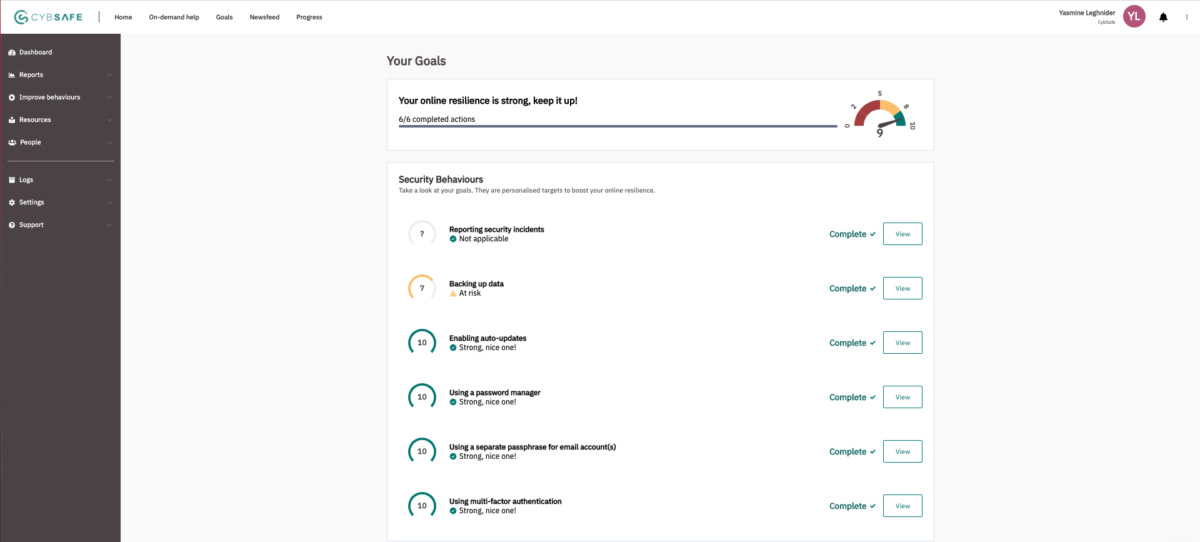
At CybSafe, we’ve packaged these steps into a handy feature. Introducing CybSafe Goals.
People using CybSafe are asked an initial question about their security behaviors. To break the goal down, they’ll see specific actions they need to complete to reach their goals in the form of an intuitive to-do list. Each action on this list links back to a security behavior within the SebDB database.
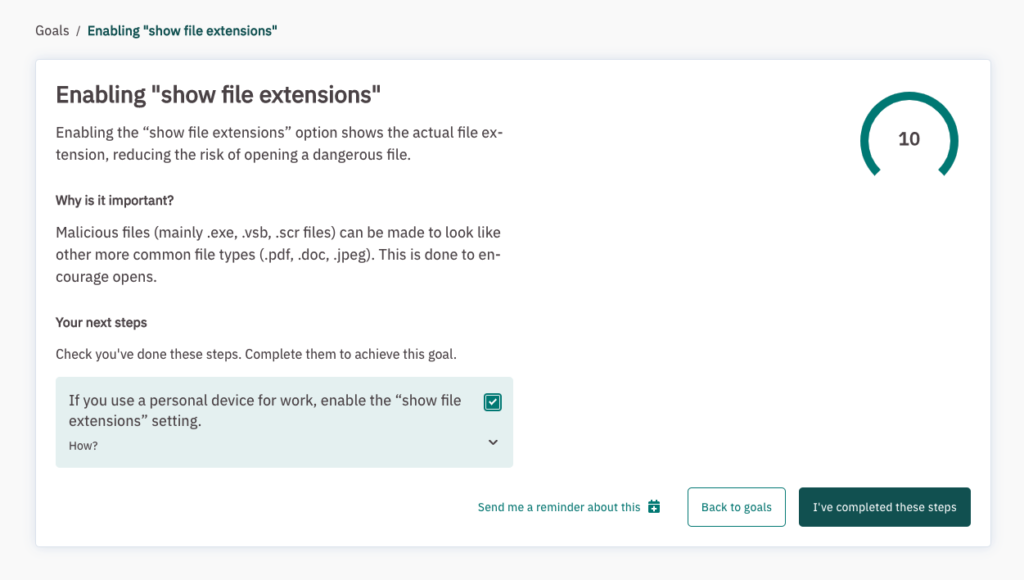
Each goal includes:
- What – a description of the goal
- Why – important of the goal
- How – next steps i.e. the action(s) required
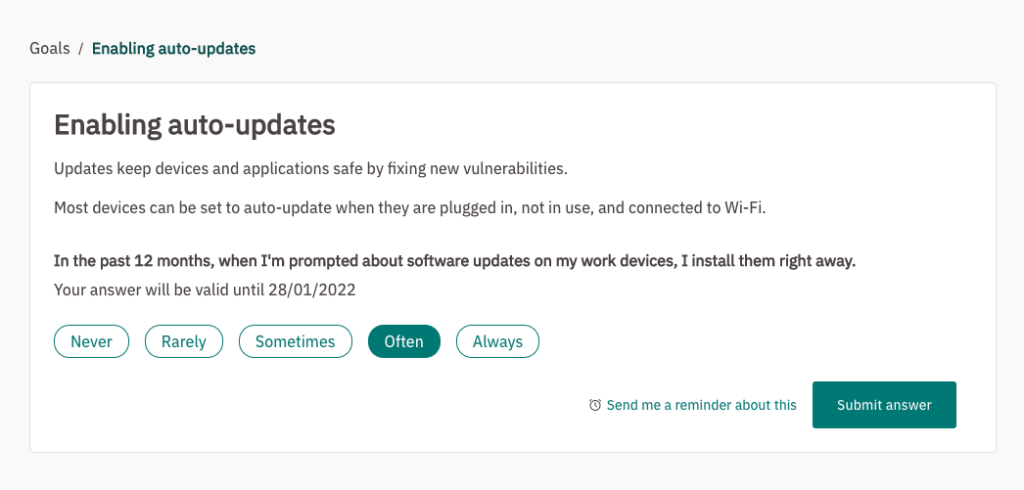
We all need a nudge from time to time, so people can set a reminder for outstanding tasks. Once they’ve completed a task, they can mark it as complete by checking the tick-box (the best feeling ever!) Each goal is time bound and has a validity period, or the number of days until their response expires. This depends on how often the action needs to be taken.
Here’s a sneak peek of what a goal looks like:
What’s next?
Setting cybersecurity goals, showing people how to achieve their goals and asking them to tell you whether they’ve completed their related next steps is an awesome step in the right direction for behavior change.
What happens afterwards?
How can you make sure the goals have a long term impact on behavior?
After all that hard work, you don’t want people to end up in the 92% of people who abandon their goals.
The data you collect from goals has massive potential to improve cyber resilience at your organization. This is where the “prompts” from The Fogg Model come into play. If you need people to do hard things, you’ve got to prompt them when there’s a motivation wave, not after the wave has subsided.
You can do this by gamifying cybersecurity programs at your organization. You can create leaderboards and incentivise goal completion. People are more likely to complete goals if there is an element of social proof. There is also the potential of sending personalised communications based on action or inaction.
At CybSafe, we are just getting started. We want to explore the behavior change space further. There’s so much potential for technology to encourage positive and long term security behaviors. Watch this space…
You can see Goals in action in our demo below:
https://www.youtube.com/watch?v=PvoHWCMztY0
If we’ve piqued your interest in behavior change, you can find out more about security solutions in our whitepaper.