Human risk management:
The definitive guide
Meet the trail-blazers redefining the security awareness & training space…for good!
![CYBSAFE-HRM imagery-230830MS [Recovered]](https://cdn.www.cybsafe.com/wp-content/uploads/2023/09/CYBSAFE-HRM-imagery-230830MS-Recovered-1.webp)
Part 1: It’s all talk
Talking about risk in the security awareness or human risk management space is nothing new.
Measuring some aspects of risk and showing risk scores is nothing new.
Truly quantifying risk (i.e., risk quantification) in the security awareness and human risk management space is new.
You can’t quantify risk if you’re not taking a view on likelihood and impact. Without solid metrics for these two elements, you are not doing risk quantification. You are simply showing risk-related metrics and scores.
If you don’t understand this, you don’t understand risk quantification.
That’s okay. Move over for people who do.
We’re getting ahead of ourselves.
Let’s roll it back.
PART 1
It’s all talk
A reliance on compliance: How we got here
Security awareness and training (SA&T) was formalized over four decades ago—by early pioneers like SASIG’s Martin Smith. As internet usage blossomed, and organizations moved online, more internet connected tools were created. The expanded digital footprint created opportunity for would-be cyber attackers.
These novel nuisances of “computer crime” and “computer hacking” needed attention.
Security awareness training was developed to show staff how to identify malicious attachments, and how to properly handle and dispose of sensitive online information. This new need for training was quickly enshrined into multiple regulations and standards.
SA&T, as it stands, is largely compliance driven, with 56% of leaders agreeing compliance is the most important indicator of SA&T success. This makes sense in terms of ticking obligatory boxes, but it doesn’t actually tackle the issue at hand: cyber risk.
SA&T can’t, and shouldn’t, sit still, because the threat and technology landscapes are ever-changing.
But are compliance regulations keeping pace?
No. They are not.
A recent piece by Jinan Budge, VP and Principal Analyst serving Security & Risk professionals at Forrester, found most regulations and standards to be “largely outdated and rarely updated”. More worryingly, many of them confuse and compel organizations toward compliance as a strategy.
SA&T should be a method, not the outcome—a brick in the wall, not the wall itself. Other bricks are needed to build a comprehensive, wrecking-ball-proof security strategy.
SA&T is like bringing a feather duster to fight where the other side is armed with AH-64 Apache attack helicopters
Our argument has always been that security strategies should be driven by…well…security! But we accept that up until now, the methods, models, technology, and understanding haven’t been there.
Thankfully, things are changing. Technology has advanced. So too has our know-how, and access to data. Meanwhile, tools like machine learning and AI continue to advance, exponentially.
Less thankfully, cyber criminals are keeping pace (and then some). They adapt, learn, and adopt the same technologies and tactics as we do. We’re in an arms race. And SA&T is like bringing a feather duster to fight where the other side is armed with AH-64 Apache attack helicopters.
PART 1
It’s all talk
Human risk management (or whatever you call it)
In a bid to face this dastardly sophistication head-on, organizations are turning to human risk management (HRM). Human risk management is a relatively new term. The practice of HRM has been developing and breaking out from the constraints of the SA&T space for several years.
You might have heard it referred to as “Security behavior and culture programs” (SBCP), or “Human detection and response”. Whatever you call it, the differences between HRM and SA&T are stark.
We’ll dive into the details later. For now, know this:
-
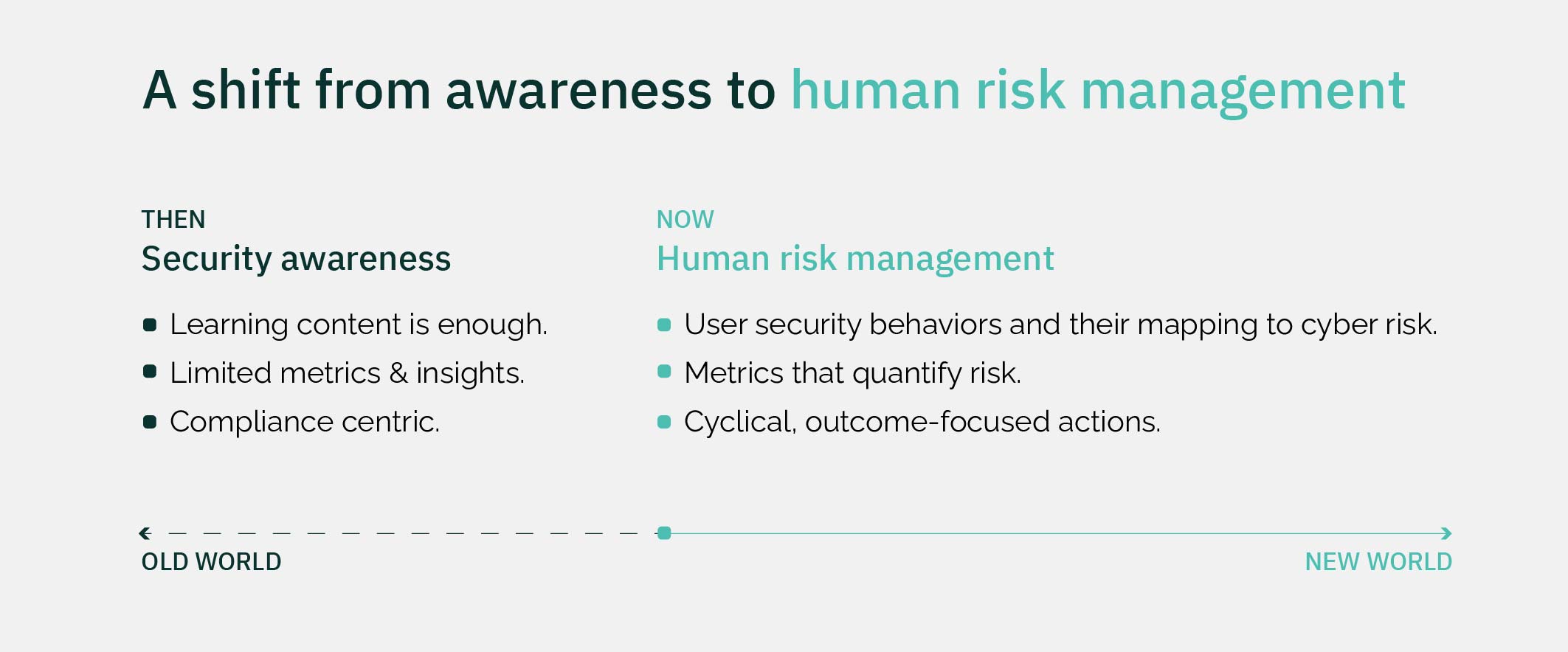
- Old school SA&T programs are centered around: learning content (being enough), limited metrics, and compliance.
- Human risk management shines the spotlight on: user security behaviors and their mapping to cyber risk, metrics that quantify risk, and cyclical, outcome-focused actions.
PART 1
It’s all talk
These wolves look like sheep!
Forgive us, for we are going to labor this point a moment longer.
It’s important because some (vendors, consultants, etc) will tell you they “do human risk management”. Some absolutely do. Others will dress up basic “activity metrics” as “risk metrics”.
If what you are looking at gives you an educated glimpse into the future (i.e., it shows you the possibility of an event occurring), it is a risk metric. If it doesn’t, it’s likely an activity metric.
Here’s a litmus test to determine if something is a true risk metric, or whether it is something else: if what you are looking at gives you an educated glimpse into the future (i.e., it shows you the possibility of an event occurring), it is a risk metric. If it doesn’t, it’s likely an activity metric.
-
- Risk metrics: A metric that measures the probability of something occurring, such as a behavior, an event, or a risk outcome.
- Activity metrics: Something that has taken place, like training completion, webinars attended, tests, clicks on simulated PHISHing emails, # of security incidents reported, dwell times, etc.
- Risk metrics: A metric that measures the probability of something occurring, such as a behavior, an event, or a risk outcome.
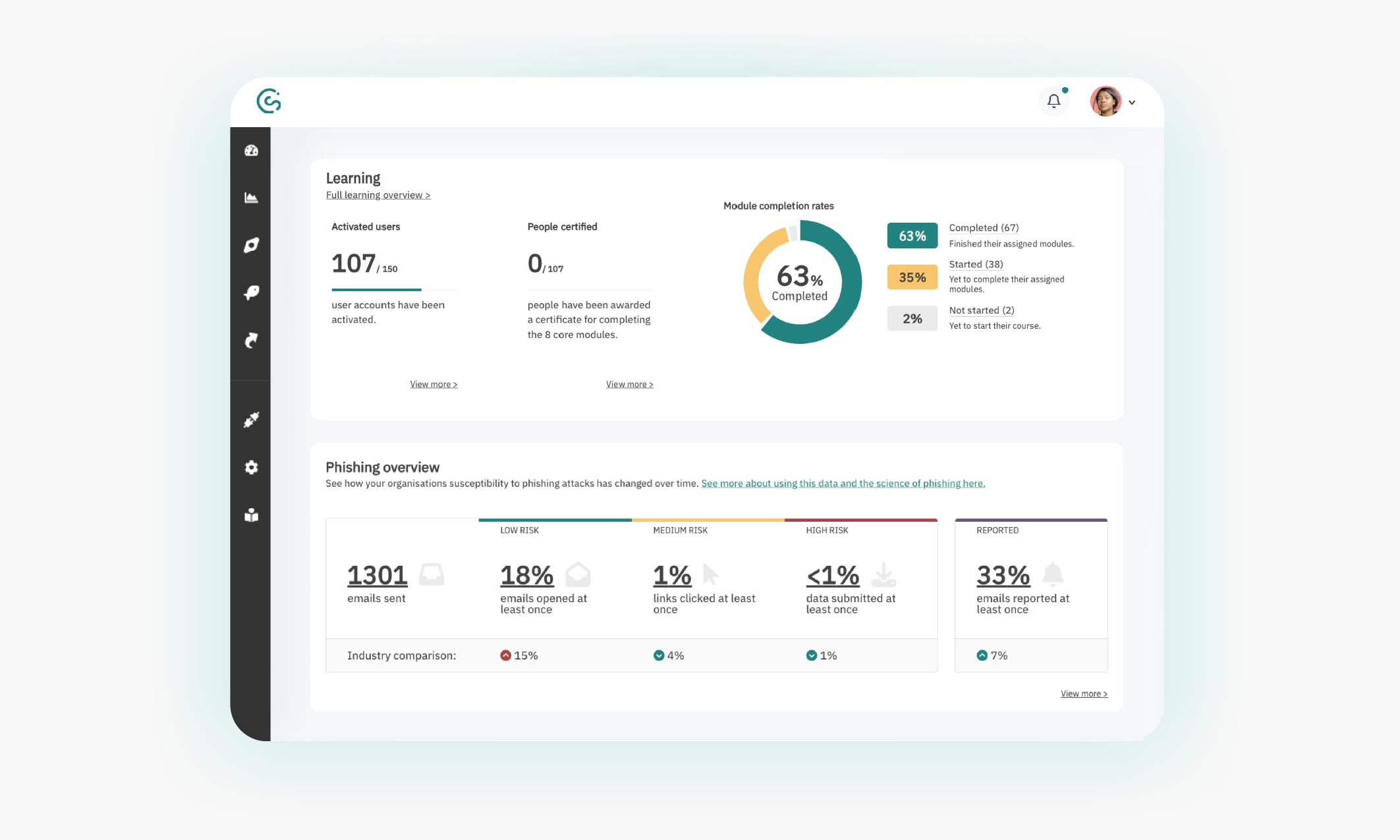
Image: A CybSafe report showing basic activity metrics
PART 1
It’s all talk
All change please: The case for human risk management
It won’t have escaped anyone’s notice, the world has changed of late. Lots.
Networks, workforces, and security teams have become decentralized. We’re remote, we’re hybrid, we’re flexible, and we’re spread all over the world.
Big data keeps getting bigger. Even small organizations now have access to eye-watering amounts of data, through third-party tools and partners.
The mass and speed of technology growth continues to compound (AI, anyone?). Today’s modern tech can do amazing things. It can also cause cognitive overload for security teams, as they operate, maintain, and keep safe, numerous tools and systems.
The need for something “better” is clear. Human risk management is that better. HRM seizes on the new technology, the access to data, and our developed understanding of science. It allows us to measure, predict, and manage the risk presented to our organizations through the actions of our people.
This includes identifying early indicators of future vulnerabilities and risk outcomes. It allows you to turn data into insights that can identify both risks and opportunities.
PART 1
It’s all talk
In(tegrate) it to win it
To combat the fatigue felt by security teams as a result of protecting their networks on a myriad of fronts, organizations are turning to “Cybersecurity mesh architecture” (CSMA) strategies.
Gartner coined the term “cybersecurity mesh” to define the integrated approach that protects assets in a network, by building layers of security to connect all of the tools used across the network.
CSMA provides a common structure for integrating tools from various vendors into a cohesive defense posture.
Human risk management is no exception. Your HRM platform should integrate with the rest of your technology stack. It should make use of the data you already have at hand. And it should work without constant human oversight. If not, it’s likely adding unnecessary pain.
Time, money, and resources are already being spent on activities to reduce human cyber risk. Standardized tools and methods allow security teams to improve and prove the impact of their work—bridging a chasm that often gives decision makers a reason to say, “no”.

Image: The integrations available to CybSafe customers
Let’s put it another way. Why would you not make the most of the data and tools you already have at your disposal? It’s nothing short of short-sighted, no?
PART 1
It’s all talk
We ❤️ compliance
This section is short. But it’s important. So we gave it its own subtitle.
Compliance frameworks guide us to get the fundamentals right. Regulatory compliance protects systems and customers from harm. Adherence to industry standards demonstrates a level of commitment. HRM is absolutely part of that process. Integral, in fact.
PART 1
It’s all talk
Necessarily urgent
The urgency in adopting human risk management is clear.
Well-meaning, commonly-accepted (and admittedly once-relevant) SA&T programs need to be bulldozed by security and risk leaders, in favor of a focus on managing human risk.
In its 16th annual Data Breach Investigations Report (DBIR), which analyzed 16,312 security incidents and 5,199 breaches, Verizon found the median cost per ransomware more than doubled over the past two years to $26,000. 95% of incidents resulted in a loss costing between $1 and $2.25 million.
Less than 15% of people who complete security awareness training go on to change their behavior
The same report concludes security breaches are still “overwhelmingly inclusive of the human element”.
What’s more, research by the Information Security Forum has found less than 15% of people who complete security awareness training go on to change their behavior.
Cyber insurance policies continue to be “refined”. In March 2023 Lloyds of London told its global network of insurer groups new or renewed policies must exclude nation-state attacks.
Additional responsibility is being piled on organizations to prove they are reducing risk. Not just ticking compliance boxes. We’re already seeing instances of organizations being denied payouts from their insurers.
Trust is not only key in today’s business world, it’s non-negotiable. If you’re going to service customers and hold data, you need watertight cybersecurity measures in place throughout your operation. You need to be able to put your firewall where your mouth is and prove it—which is why HRM is becoming such a huge deal.
Yet from a security professional’s perspective, this remains a hard-sell. Not least because proving the impact from the money spent on SA&T activities is, at best, difficult.
At worst, it is impossible.
Part 2: Understanding human risk
If you’re in the business of managing human risk, understanding the standard terminology used to talk about risk is crucial.
The terms “vulnerability”, “threat”, “risk”, and “risk outcome” are often used interchangeably.
This is a problem when convincing non-practitioners of the importance of implementing measures which cost money and time.
PART 2
Understanding human risk
Knowing the difference matters
We’re aware most of this won’t be new information for senior decision makers. Similarly, many risk and security teams understand risk terminology well.
But there’s a gap. A disparity between how human risk is treated compared to other areas of security risk.
The methods and modeling used to keep organizations secure elsewhere are simply not applied to the risk presented by the actions of people.
The security awareness function seems to be the only part of the security team that doesn’t have to prove the value of its work, beyond ticking a compliance box
In fact, you could go so far as to say the security awareness function seems to be the only part of the security team that doesn’t have to prove the value of its work, beyond ticking a compliance box. We won’t, though. Because that would be inflammatory.
However, it is both a concern and the reason why understanding the nuances of risk matters. So, if you’d all go grab your CISSP study guides, and turn to chapter one.
PART 2
Understanding human risk
Human risk management terminology
In this section you’ll see links to security behaviors and risk outcomes from the Security behavior database, or SebBD. SebDB is the world’s cyber security behavior database. It maps over 100 security behaviors to risk outcomes.
Security behaviors
A security behavior is any action a user takes to influence human cyber risk. It’s the things they do day-in, day-out as they interact with technology.
SebDB is maintained by a global community of security professionals and academics. It’s free to use, and can be downloaded for offline use. You can join the SebDB Community and contribute to the development of the database, here:
What is a vulnerability?
Vulnerability
A vulnerability is a weakness that exposes an entity to threats, increasing the likelihood of a negative event.
Inappropriate or suboptimal user security behaviors are potential vulnerabilities.
HRM vulnerability examples:
The vulnerability itself is not a risk, but a vulnerability might mean increased risk.
What is a threat?
Threat
A threat is anything that can exploit a vulnerability to cause damage, harm, or loss.
Threats can be intentional or unintentional.
HRM threat examples:
-
- [Intentional] Criminals exploiting people who don’t use strong passwords by conducting brute force attacks against systems.
- [Intentional] Criminals exploiting people who don’t report known or suspected incidents by calling them to elicit sensitive information.
- [Unintentional] People emailing sensitive information to personal email accounts to work on projects at home.
What is risk?
Risk
Risk is the potential for damage, harm, or loss.
In the context of human risk management, it is the potential for damage, harm, or loss to assets or data caused by a human-related cyber threat being realized.
For some, there are two sides to HRM:
-
- User-focused risk (general employees)
- Technical role-focused risk (engineers, developers, system architects, system administrators, IT technicians, etc.)
At CybSafe, when we talk about HRM, we’re referring to the appropriate management and/or reduction of user-focused cyber risk.
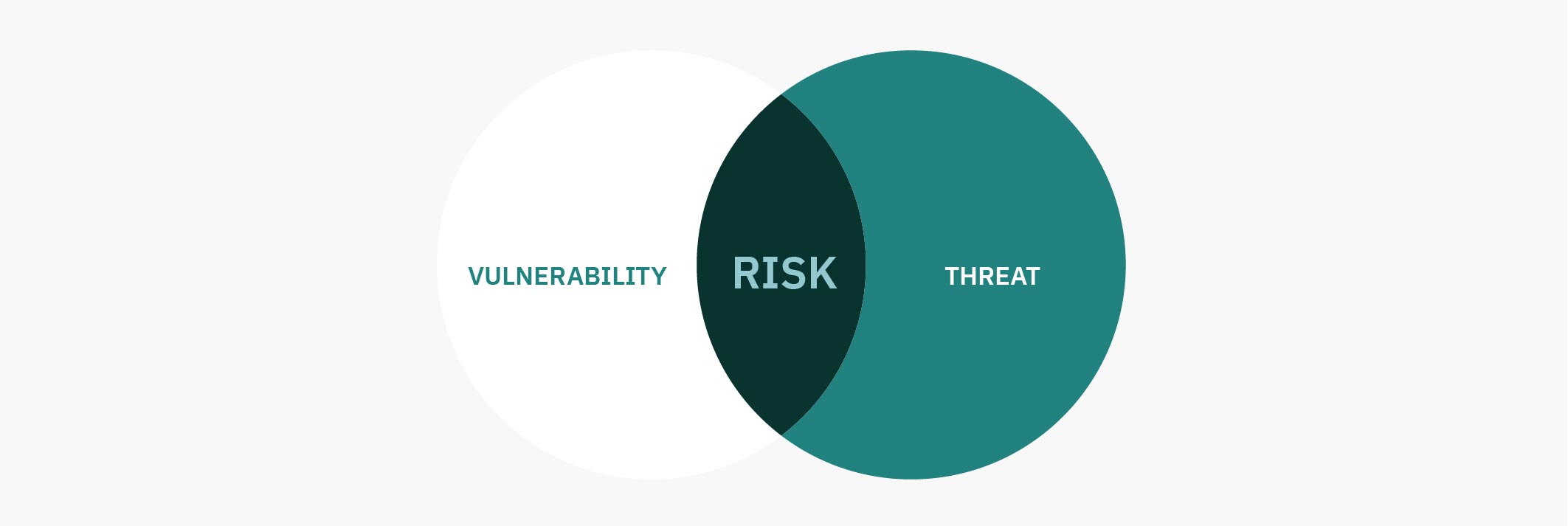
Risk sits at the intersection of vulnerabilities and threats. If you don’t have both, you don’t have risk.
For example, if a criminal calls someone to elicit sensitive information (a threat), but the person they reach has no access to sensitive information, there is no vulnerability, and therefore little to no risk.
The level of risk an organization faces is often referred to as its “risk profile”. Risk profiles change based on the potential or probability of negative events, but also the impact events may have on an organization.
Different organizations have different tolerances and appetites for risk. It explains why, in risk analysis, risk is defined as a function of likelihood and impact.
What is a risk outcome?
It’s important to be specific when talking about risk. When we say we are concerned about risk, we must be concerned about something in particular.
Risk outcomes
A risk outcome is that particular something. It’s the actual result if risk materializes.
Risk outcomes are the things most organizations and security teams are keen to avoid.
HRM security risk outcomes:
PART 2
Understanding human risk
So, what exactly is human risk management?
Understanding risk sits at the heart of HRM.
Not all risk is equal, and management of risk requires prioritization. Some risk will be acceptable. Some won’t.
The process by which we categorize risk, and the steps we take to mitigate it is human risk management.
In order to understand HRM we need to understand human cyber risk.
Human cyber risk
Human cyber risk is the extent to which an organization is exposed to loss or harm because of their people’s security attitudes, situational awareness, knowledge, decisions, and behaviors.
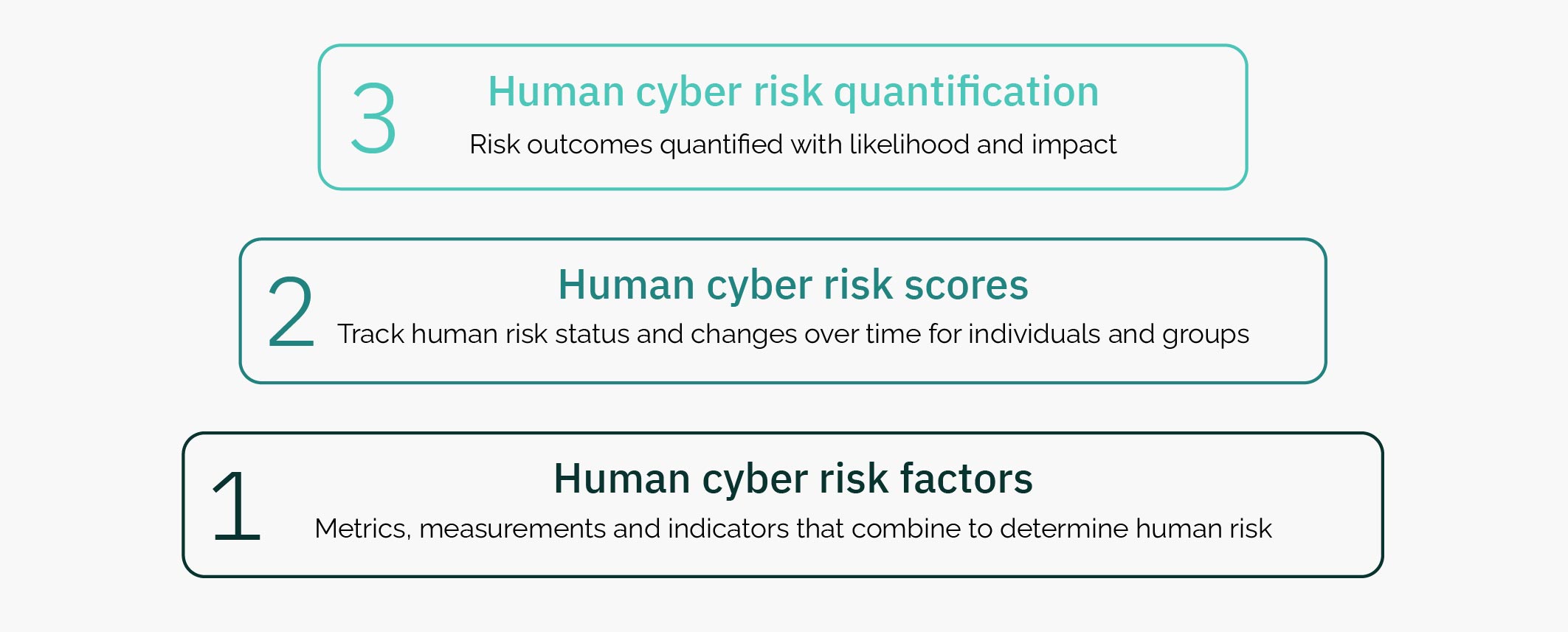
The likelihood of risk outcomes occurring is based on a variety of “human cyber risk factors”. Scores can be applied to human cyber risk factors to track changes over time for individuals and groups. And these scores can be aggregated to quantify the likelihood and impact of risk outcomes.
So, we’re going to nail our colors to the mast and say…
Human risk management
Human risk management is the identification, evaluation, and prioritization of user-focused cyber risks, followed by coordinated and effective application of resources to minimize, monitor, and control the likelihood and impact of unwanted cyber incidents, or to maximize the realization of digital opportunities.
And as a (not insignificant) bonus, it doesn’t cripple budgets, productivity, or your staff’s mental wellbeing in the process.
PART 2
Understanding human risk
We’re talking about my principles!
We discussed the main differences between SA&T and HRM earlier. As you’ll have recognized by now, human risk management is a different approach, built on a number of principles.
Human risk management principles:
-
- When it comes to users, there is more to risk reduction than awareness, knowledge, education, & training.
- Awareness, knowledge, education, & training are not enough to change behavior in a sustainable way.
- HRM strategies and initiatives go beyond SA&T, taking all possible steps to increase the chance users behave securely, or reduce organizational risk.
- Research and data underpin HRM decisions and actions.
- Robust metrics, data, and reporting are the cornerstone of any HRM approach.
- Risk reduction and risk management are the primary aims, necessitating a more mature understanding of risk.
- HRM seeks to maximize efficiency, integrate tools, and automate wherever possible.
- HRM favors approaches and activities that are automated, scientific, and measurable.
Right! That’s what it is, and that’s how to approach it.
It’s time to get our real geek on, and dig into each level. This is where things get interesting…
(Yes. It was a Friends reference.)
PART 2
Understanding human risk
LEVEL 1: Human cyber risk factors
This is the foundation for all HRM, and yet it’s so often misunderstood.
Human cyber risk factor
A human cyber risk factor is something that increases or decreases the chance of an individual becoming victim of a successful cyber attack, and unwittingly contributing to a cybersecurity incident.
Many people think the only human cyber risk factors are:
1. Knowledge & understanding
2. Security behaviors
In order to equip people with the Knowledge & understanding they need, organizations lean heavily on:
-
- Training modules
- Emails
- Intranet posts
- Videos
- Newsletters
- Quizzes
- Presentations
- Webinars
- Games & competitions
And for Security behaviors, they fixate almost exclusively on:
-
- Phishing simulations (click rates, report rates, dwell times)
Here’s our best graphic representation of what that might look like…
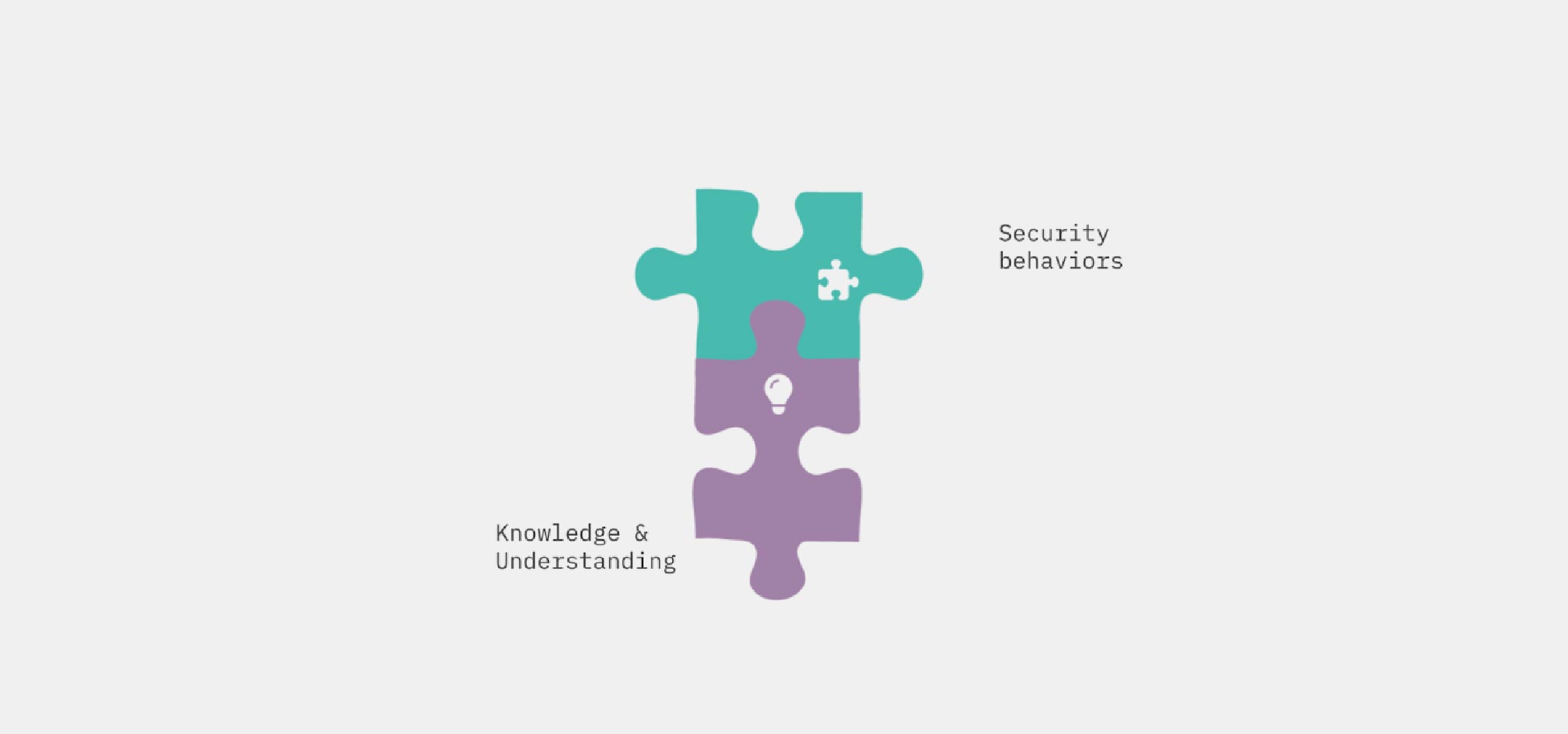
Two things are wrong with this approach:
-
- First, the full range of factors aren’t being considered
- Second, the factors are weighted so resources are apportioned inefficiently to affect meaningful change to risk
Managing human risk is multifaceted. It requires the bringing together of both technical and non-technical disciplines.
This includes behavioral science, technology, neuroscience, computer science, data science, business management, psychology, cybersecurity (offensive & defensive), artificial intelligence, communication, and—everybody’s old favorite—learning & development.
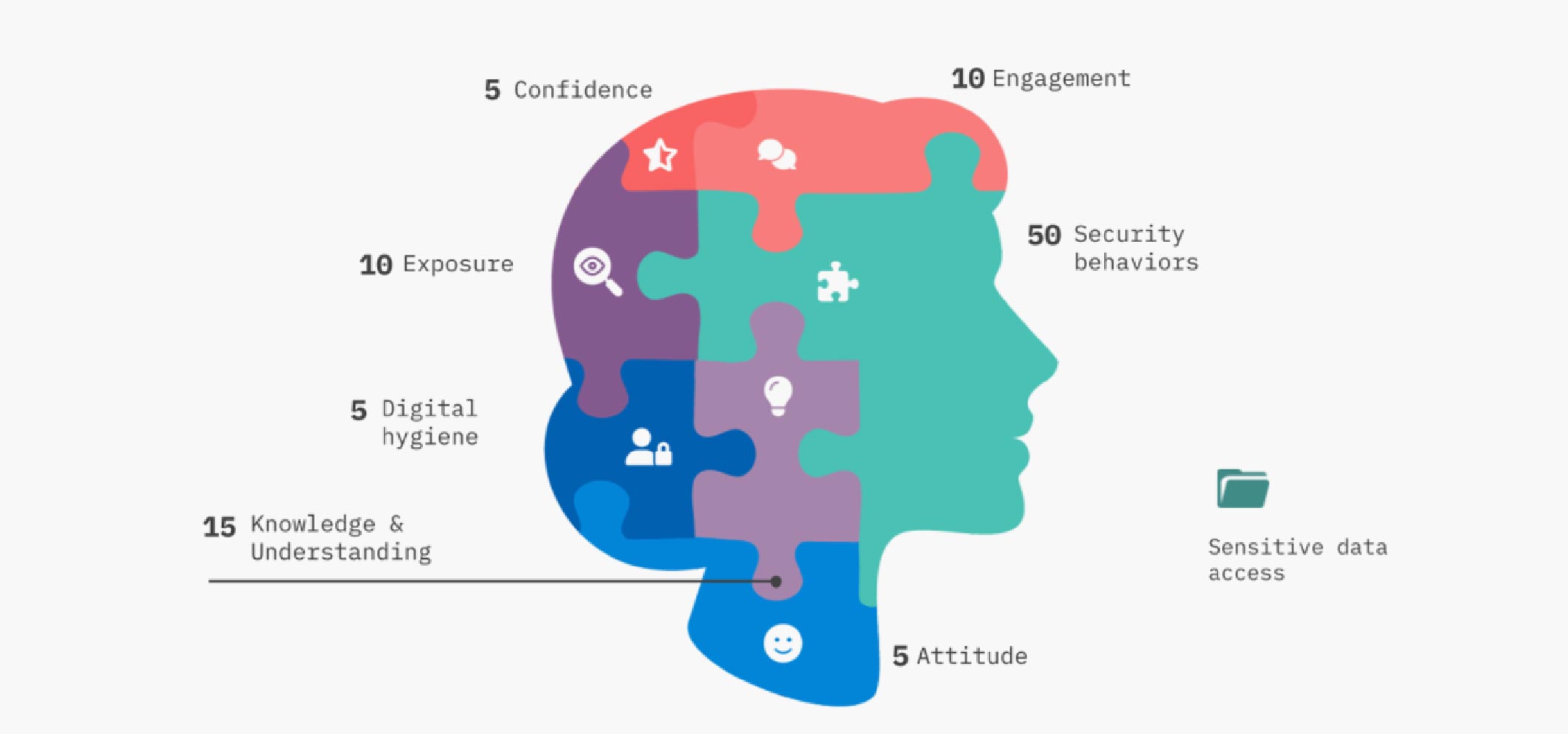
In reality, a number of additional human cyber risk factors matter:
1. Knowledge & understanding (15%)
2. Security behaviors (50%)
3. Attitude & sentiment (5%)
4. Engagement (10%)
5. Confidence (5%)
6. Exposure (10%)
7. Digital hygiene (5%)
~~~
8. Sensitive data access
A quick note on Culture:
Organizational security culture is worth considering, and important to measure and improve where possible.
However, we recognize “security culture” is defined differently in different organizations.
There is no right or wrong, per se. But it’s important to be clear what culture means to your organization before you attempt to measure it, or your measurements won’t mean very much.
Why do risk factors have percentage weightings?
Some factors are more important than others. That’s why we weight them accordingly in our risk calculations.
The weightings reflect our current understanding of how much each risk factor plays in the likelihood of an individual falling victim to a successful cyber attack.
(The CybSafe Science & Research team regularly evaluates the weightings through research and analysis of data as it is generated by the CybSafe platform. We’ve built our technology to be able to make changes as and when we need to.)
None of this “people are the weakest link” bollocks
In this approach, security behaviors are given their rightful place at the table. None of this “People are the weakest link” bollocks, mind you.
As we continue to see year-on-year, people are cited as the main factor in security breaches. But this language isn’t helpful when talking about human beings.
If you mean “People are important because how they behave has a disproportionate effect on our organizational risk”, then just say that. And, apportion the appropriate amount of time, money, and resource to mitigate it!
It’s why, in our modeling, security behaviors account for 50% of the total weighting.
What about sensitive data access?
The eagle-eyed among you will notice “Sensitive data access” doesn’t have a percentage weighting.
Think of sensitive data access as a “force multiplier”. Individuals in high-risk roles, with access to sensitive data, have potential to do more harm to an organization.
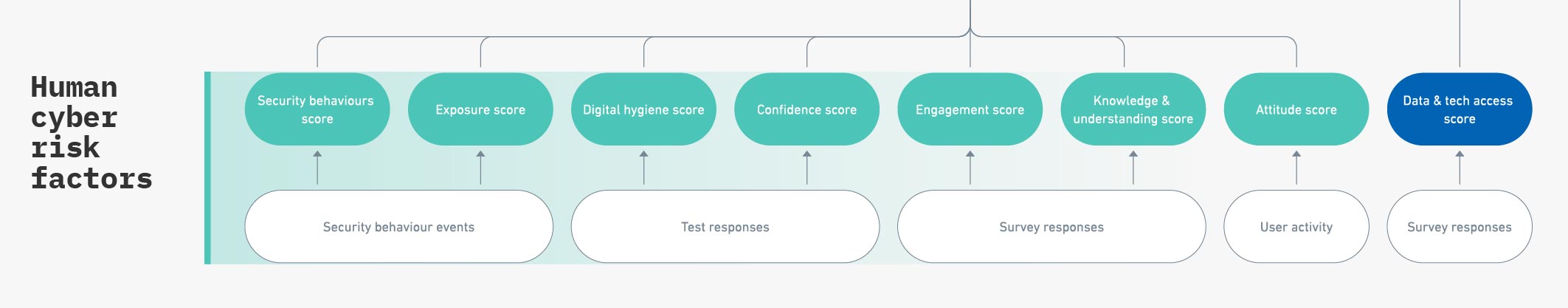
Measuring human cyber risk factors
Human cyber risk factors are calculated through a series of objective and subjective data collection processes.
Objective processes:
-
- Security behavior events captured by the CybSafe platform and other integrated cloud-based productivity suites, communication tools, and security tools (like Google Workspace, Microsoft applications, Crowdstrike, etc.)
- Test responses
- User activity
Subjective processes:
-
- Self-selected confidence scores
- Survey responses
Risk factors are calculated at the individual user level, and aggregated with averaging scores for the required group or organizational level.
The score for individuals in high-risk roles, with access to sensitive data, are modified. It means these people have to be more diligent in their work to obtain “good” scores. With great power comes great responsibility, as they say!
PART 2
Understanding human risk
LEVEL 2: Human cyber risk scores
Armed with our understanding of human cyber risk factors (an upgrade to our feather duster), we can build accurate human cyber risk scoring systems.
Scores track the change in risk status at individual, team, and organizational levels.
Score can be used to show people how they’re doing, and how they compare to their peers. (At CybSafe, we’ve chosen to show scores as scorecards.)
Scores can be aggregated for teams and departments, which in turn allows comparison of your organization to others – giving you a good indication for where you might be at.
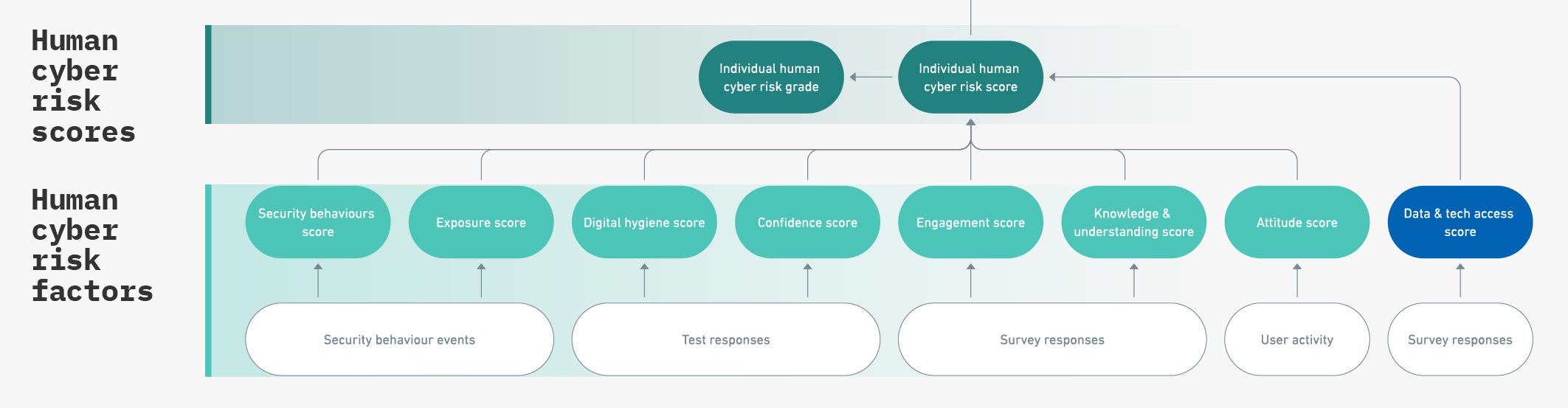
So if I see risk scores or grades, I’m quantifying risk?
No, not yet.
Scores (or grades), that do not show likelihood and impact, do not quantify risk
Attributing scores to people is nothing new.
Scores are great for determining who is doing well and who might need help. Scores measure and track progress. Scores facilitate informed decision making. But scores (or grades), that do not show likelihood and impact, do not quantify risk.
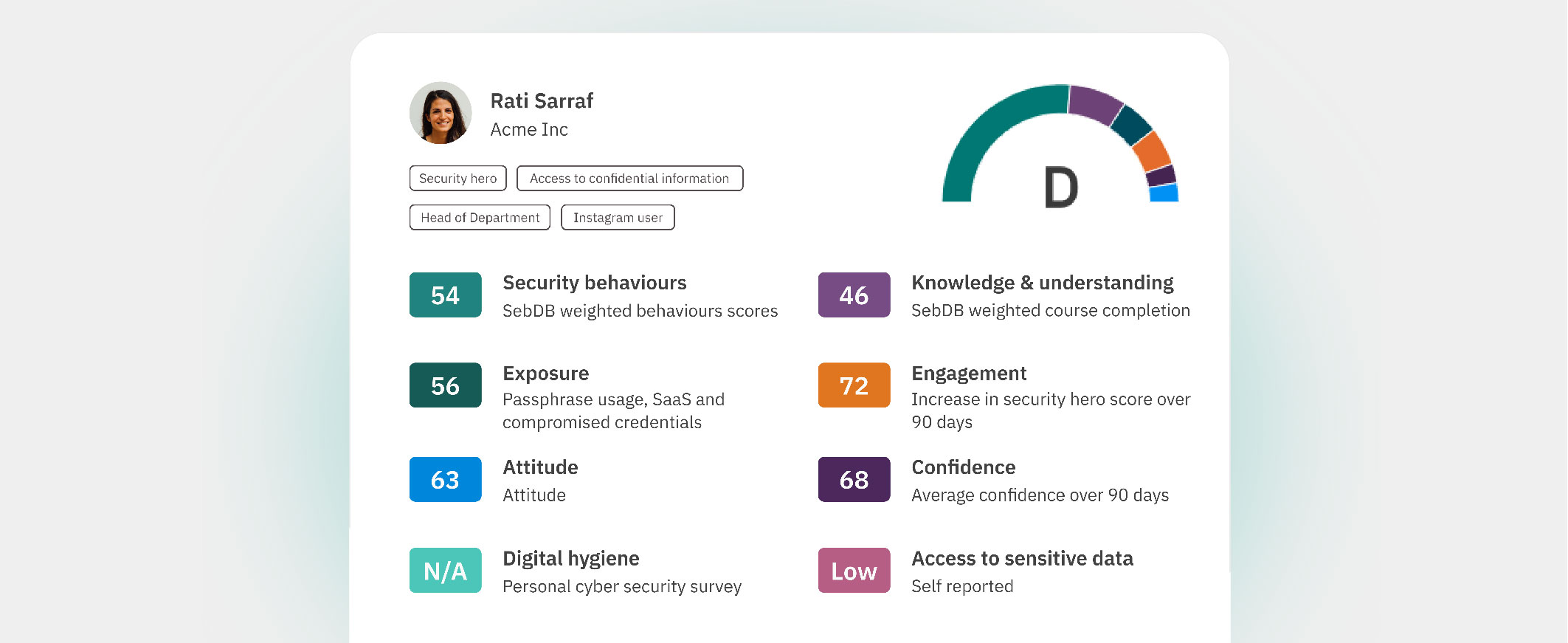
Image: A CybSafe scorecard showing an individual’s progress based on contributing human cyber risk factors.
Remember our wolves from earlier? This is as far as they typically get.
Actually, it might be as far as anyone has ever gotten. At the time of writing, we know of no other organization, consultancy, or vendor that has developed a human cyber risk quantification model, let alone built it into an automated software product.
From here on out, we’re venturing into uncharted territory.
You ready?
PART 2
Understanding human risk
LEVEL 3: Human cyber risk quantification
Level 3 sees our risk scores – which were developed from our risk factors – combine to calculate the likelihood of each risk outcome occurring, and the impact that outcome might have.
-
- Likelihood: The probability a given risk outcome will occur
- Impact: The extent to which a risk outcome might affect the organization
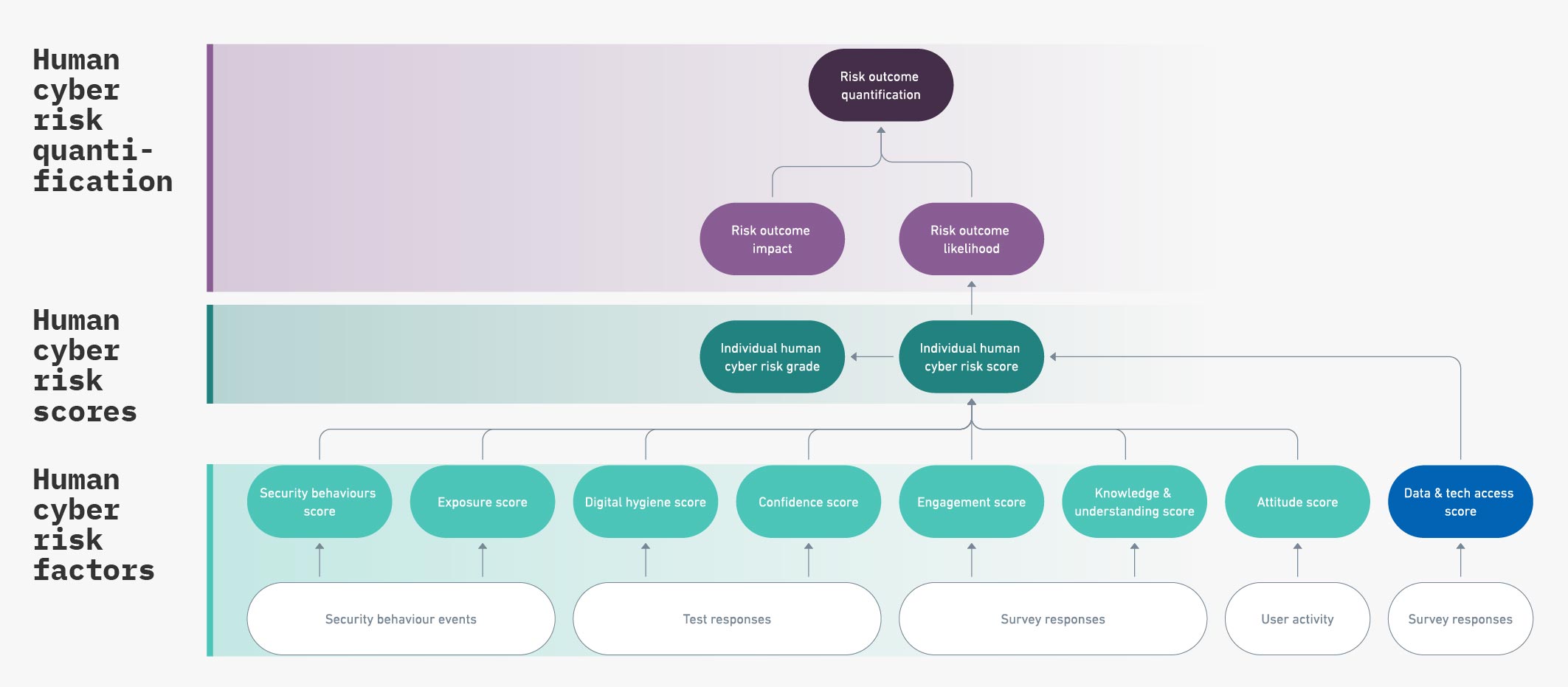
With likelihood and impact combined, we are able to quantify human cyber risk.
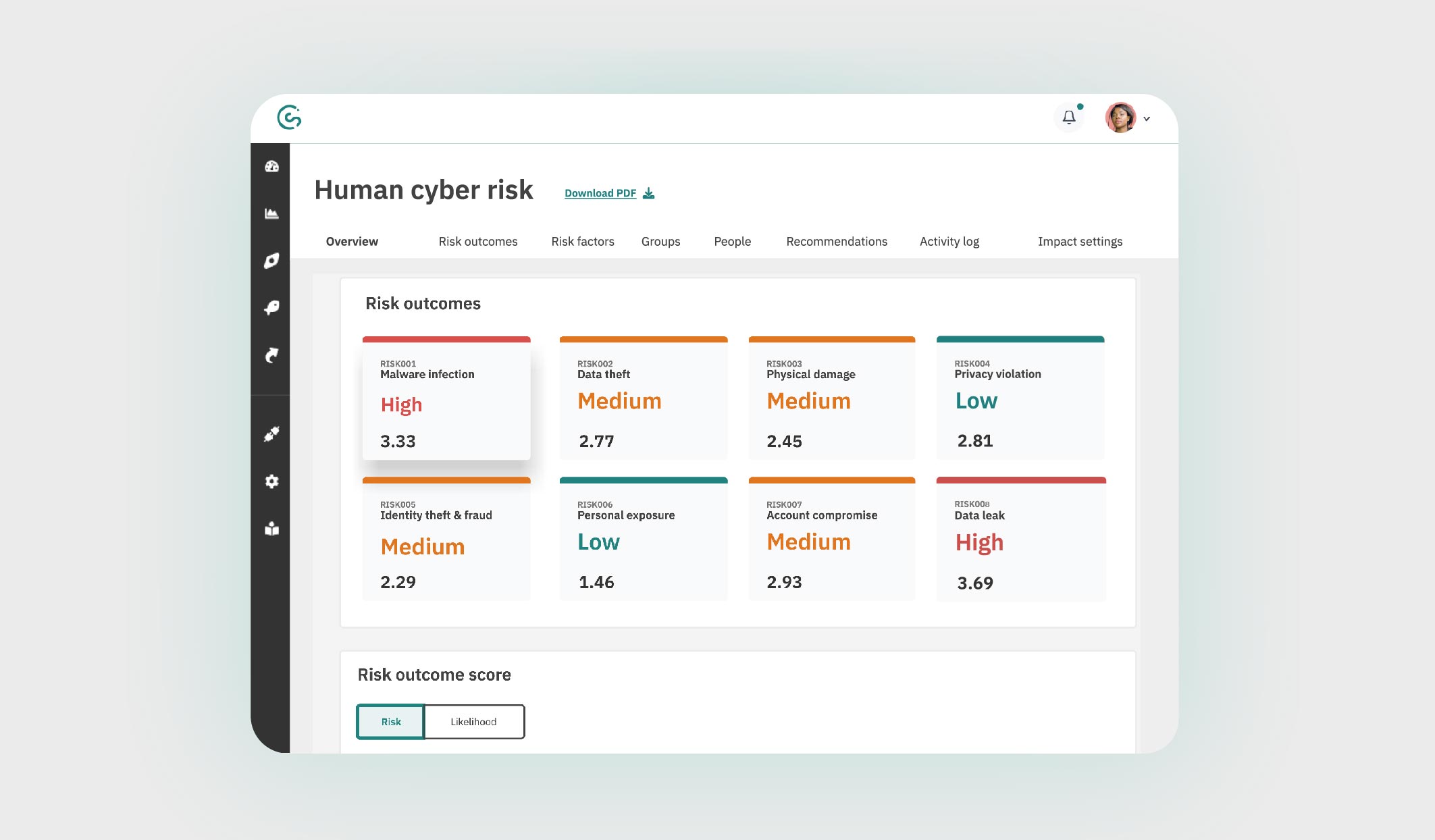
Image: The CybSafe human cyber risk dashboard. An industry first.
We’ve already seen how organizational risk profiles can change depending on internal and external factors. A couple of examples:
At CybSafe we predict likelihood based on behavior event intelligence data from the CybSafe platform and other integrated systems.
Impact is determined based on a series of settings, which can be configured by each organization.
This is important because $1m for one organization could be the difference between survival, and total failure. Whereas for another organization, it might represent nothing more than an inconvenience.
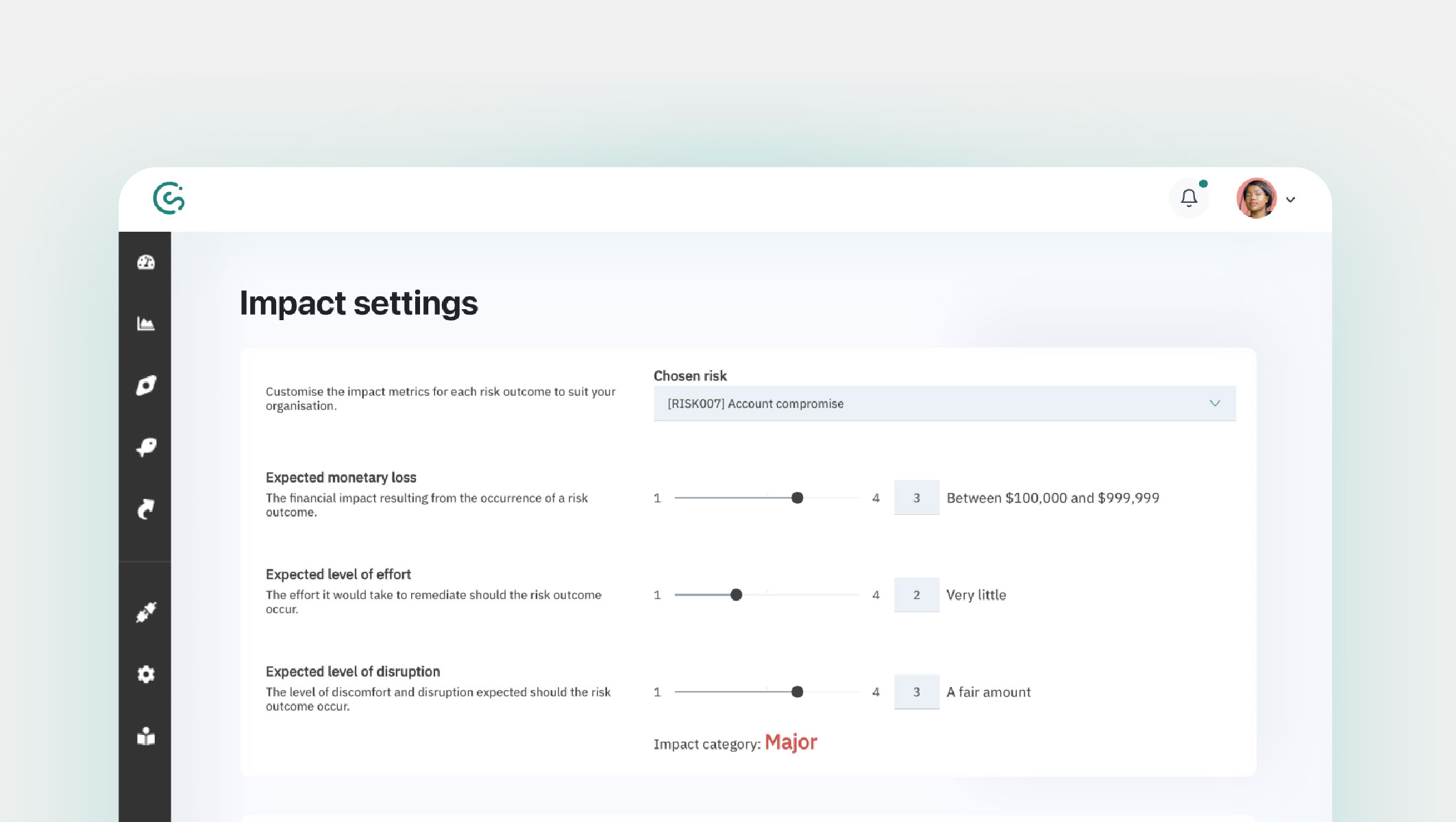
Image: The impact settings page.
PART 2
Understanding human risk
Pause. Summarize. Continue.
That’s a lot to have taken in. So, to recap:
-
- The likelihood of risk outcomes occurring is based on a variety of human cyber risk factors.
- Scores can be applied to human cyber risk factors to track changes over time for individuals and groups.
- And those scores can be aggregated to quantify the likelihood and impact of risk outcomes.
This brings us to the end of our TED Talk. Thanks for listening.
Stick around though, we’ve saved the most electrifying part for last…
Part 3: What this means for you
We can take the truth. We know you’re not reading this for fun. Y’all want to know what it means for you.
And we want to tell you.
Once you understand and leverage human risk management, what can you do? How do you know you’ve arrived?
1) You can model human cyber risk—and use the models to make informed decisions
By integrating quantification into your decision-making process, you gain a comprehensive view of your organization’s user-focused vulnerabilities.
This empowers you to not only anticipate risks, but also strategize effective interventions, ensuring proactive security measures.
2) You can put a monetary value on human cyber risk
Imagine a realm where discussions about human cyber risk aren’t just theoretical; they’re concrete, data-driven, and actionable.
It’s not about merely showcasing numbers; it’s about quantifying the risks you face and attaching a tangible, monetary value to them.
Savings. Cost reduction. A positive impact on profits. Boards love this.
3) You know the value of your security awareness initiatives
Bid farewell to uncertainty. Quantified human cyber risk lets you measure the impact of your security awareness initiatives – and demonstrate their value.
No longer are you left (secretly) wondering if your efforts make a difference. With quantifiable insights, you can prove a clear ROI of your work.
4) You know how much you need to invest and where you need to invest it to protect future revenue
Enter the age of strategic investment. With quantified human cyber risk, you have a roadmap for optimal resource allocation.
No more speculating. Strategically fortify your organization against potential threats, and safeguard revenue streams.
5) You can save money, time, and resource
By modeling the potential effectiveness of various interventions, you can conduct cost-benefit analyses. This leads to more effective uses of money, time, and resource. Exciting, right?
So, that’s the why nailed down. For the how, we turn to a stand-out, bona fide, enlightened-af, trailblazer.
PART 3
What this means for you
On the Hunt for probabilistic human risk modeling
Ash Hunt is the Global CISO at Apex Group. He approaches risk management like the seasoned strategist he is.
Ash puts his unique approach to cybersecurity down to his extensive, cross-sector experience. (It also doesn’t hurt that he wrote the UK’s pioneering quantitative framework for information risk, too.)
On a recent episode of the Behave podcast, Ash dissected the myriad of potential pitfalls that can derail an organization’s security objectives.
“There are things that can prevent this organization from achieving its objectives, and when I look at those things sometimes they can be many.
There’s a lot of potential things that can go wrong with a business. My job is to help work out, out of the things that are relevant to preventing us from achieving those objectives, which of them are most probable to cause us the greatest amount of failure? Looking at how often bad stuff happens and, within a range, how much damage it causes each time it does.
And when you take that bottom-up approach, mathematically aggregating those views is super straightforward.”
When considering risk, it’s easy to feel like you’re drowning in a sea of uncertainty. But Ash proves you can navigate a clear path through.
Ash Hunt believes probabilistic human risk modeling is the key to accurate and reliable human risk management.
He likens traditional risk management methods to shooting in the dark, as they’re often based on subjective judgment (if we’re being kind), and guesswork (if we’re being real).
Probabilistic human risk modeling, on the other hand, is like using a sniper rifle. It uses data and analysis to estimate the probable impact of risk and associated interventions. This gives organizations a more robust understanding of what they’re up against, and what they can do to mitigate.
Transformational CISOs and their security teams are turning to probabilistic human risk modeling as their default way of doing things.
One such organization is NASA. They continuously run multiple risk methodologies against each other on all of their decision-making.
Granted, not all organizations are faced with the risks of sending people to space. But Hunt is clear. Probabilistic risk modeling can help any organization to:
-
- See the forest from the trees: By identifying the most likely vulnerabilities and threats, organizations can focus their resources on mitigating risk, and avoid wasting time and money.
- Speak the same language: Probabilistic risk modeling uses a common language—probability and financial figures—that everyone can understand. This helps to break down silos and build trust between different departments and stakeholders. It is especially useful when speaking with boards and decision makers.
- Stay ahead of the curve: By monitoring and updating their models, organizations can ensure they are always aware of the latest risks, and are taking steps to mitigate them.
Probabilistic human risk modeling is the best way to keep organizations safe in today’s complex and ever-changing world, Hunt says. It’s well worth listening to the whole, fascinating episode.
PART 3
What this means for you
Getting started: Real-world use cases
How about some tangible ways HRM practices can transform an organization? These are just some of the benefits of applying a scientific, research-backed approach to your work.
1. Anticipate risky user behavior: Identify patterns of risky behavior, such as clicking on phishing links, sharing passwords, or downloading unauthorized software.
2. Provide personalized training: Individual or group risk profiles can be used to create personalized training, tailored to the specific needs of each employee or employee group.
3. Identify vulnerabilities: The Security behavior database can be used to identify specific risk areas and associated security behaviors that require attention.
4. Quantify human cyber risk: Analytics can be used to quantify an organization’s human cyber risk profile. This information can be used to make informed decisions about resource allocation and cybersecurity strategy.
5. Translate data into strategic action: Data can be used to craft compelling narratives around human cyber risk for stakeholders. This information can be used to secure investments for cybersecurity initiatives, and showcase the value of the security function within the organization.
6. Foster continuous improvement: Track human cyber risk over time, both at individual and group levels, and identify areas where security initiatives can be fine-tuned.
The message is clear: HRM practices protect organizations from cyber attacks, bolstering their overall security posture.
How can you make the strategy a reality, without creating a ton of work for you and your team?
PART 3
What this means for you
CybSafe: It ain’t bragging if you back it up
We didn’t just throw this page together in a day or two. What you have just read represents years of thinking, research, testing, listening to practitioners, getting it wrong, getting it right, iterating, and picking ourselves up after every shock from the side.
Years of thinking, research, testing, listening to practitioners, getting it wrong, getting it right, iterating, and picking ourselves up after every shock from the side
We believe everyone should be able to use the online world safely. And we’re on a mission to redefine how society addresses the human aspect of security.
Here are three, indisputable facts:
-
- All organizations, across all sectors, grapple with human cyber risk
- Even minor missteps can cascade into monumental data breaches
- Conventional SA&T solutions are inadequate, leaving gaps
The status quo of SA&T is unsafe, untenable, and unacceptable in today’s world. Redefining your approach to human cyber risk is not only possible, it is essential.
Three crucial elements are at the center of the HRM approach. They are also the principles we use to build CybSafe:
-
- Scientific: Everything is underpinned by scientific research and testing from our in-house Science & Research team.
- Automated: Everything is built to quantify risk and orchestrate an automated response with the least amount of administrative input possible.
- Measureable: Every factor, every score change, every user action, and every intervention is measured, quantified, and reported on.
PART 3
What this means for you
Is my organization ready for CybSafe?
No one wakes up and just “does” human risk management. It’s a journey.
Many prospective CybSafe customers only need to achieve SA&T compliance, increase engagement, and reduce phishing & ransomware risk.
They’re pleasantly surprised to learn CybSafe does these things, and starts them on the HRM path, and does it for the same cost as their traditional SA&T provider.
GUIDE educates and engages people—while helping achieve compliance.
Customizable, and designed with the modern, remote and hybrid working environments in mind, GUIDE is the perfect start to any human risk management strategy, for any organization.
PHISH simulates modern-day threats, and supports people in lowering their phishing and ransomware risk.
To help address risk on all fronts, PHISH combines seamlessly with our other products, giving you a truly holistic approach to phishing and ransomware risk reduction.
And for those organizations who have begun their HRM journey, and are wanting to unlock the full power of their existing tech stack, we have this…
RESPOND leverages existing data, tooling, and behavior event intelligence for a wider view of risk.
RESPOND analyzes potential cybersecurity threats using existing security tools and data, nudges users, enrolls people into behavior-triggered workflows, and alerts security teams.
PART 3
What this means for you
What’s the unifying factor?
But don’t just take our word for it. We’re lucky enough to work with an awesome group of visionaries. All these organizations have seen a reduction in security incidents related to human error.
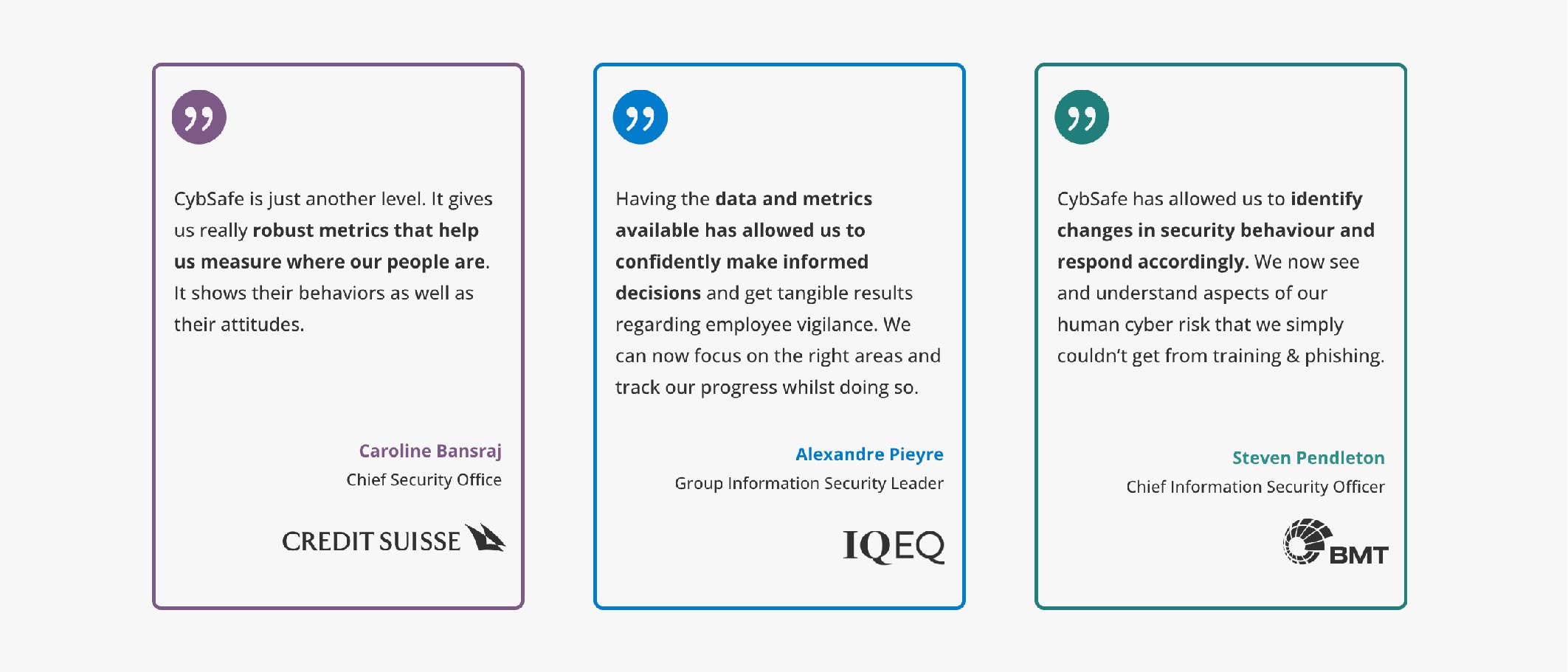
If you’re ready to experience it first hand, book a demo, and witness the transformation.
Here’s to blazing a trail.
CybSafe.




