On demand webinar ‘What (Gen)AI means for security awareness in 2024’ WATCH NOW >
THE HUMAN RISK MANAGEMENT PLATFORM
Influence specific security behaviors.
Measure risk reduction.
TRUSTED BY GLOBAL
LEADING ORGANIZATIONS
Increase in employee
cybersecurity confidence
Reduction in high-risk
phishing behavior
Improvement in
security behaviors
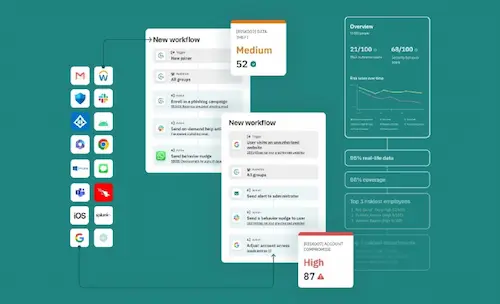
One platform.
Multiple behaviors.
Countless interventions
CybSafe does what most only claim to do—lower your human cyber risk. It’s the award-winning, cloud-based software built on the understanding that traditional security awareness and training (SA&T) doesn’t influence security behaviors. CybSafe educates, nudges, and supports your people, and gives you both measurable change and measurable value.
Traditional security awareness is dead
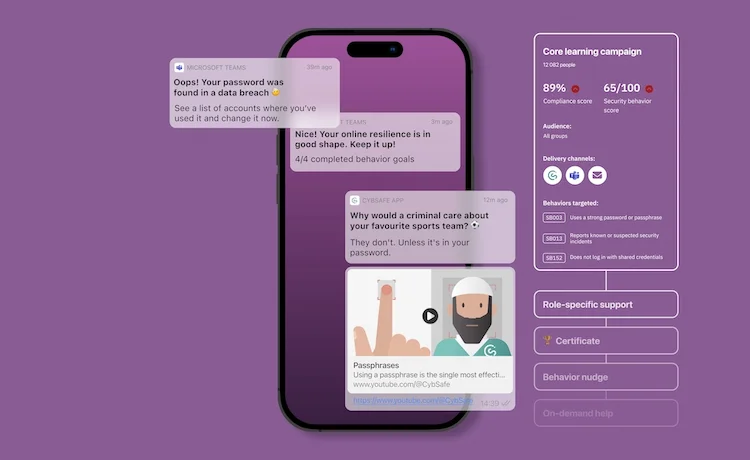
The most scientific way to provide personalized guidance, nudges, and training that influences security behaviors, reduces risk, and helps you achieve compliance—all at once.
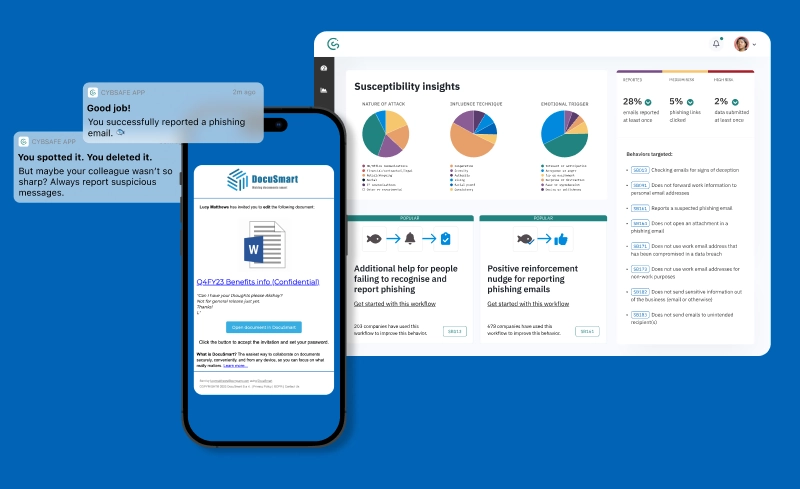
The scientific approach to reducing risky phishing behaviors
The most data-driven way to reduce phishing and ransomware risk. Run phishing simulations that tell you why and when people click—and do it with minimal friction.
The new standard in human layer security
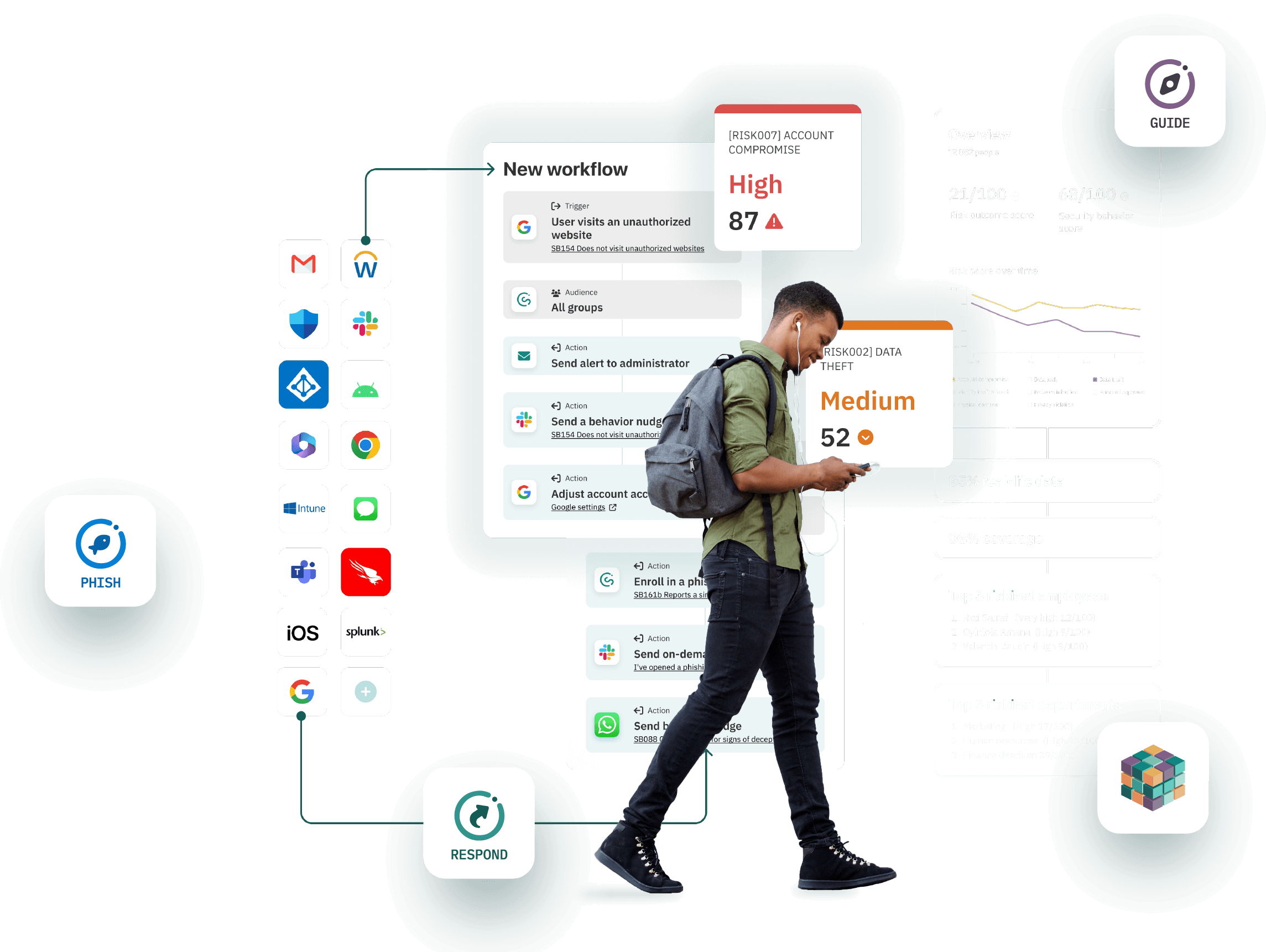
The CybSafe human risk management platform empowers you to measure, understand, target, and influence specific security behaviors. CybSafe is backed by science and powered by the world’s most comprehensive security behaviors database, SebDB. We’re trusted by thousands.
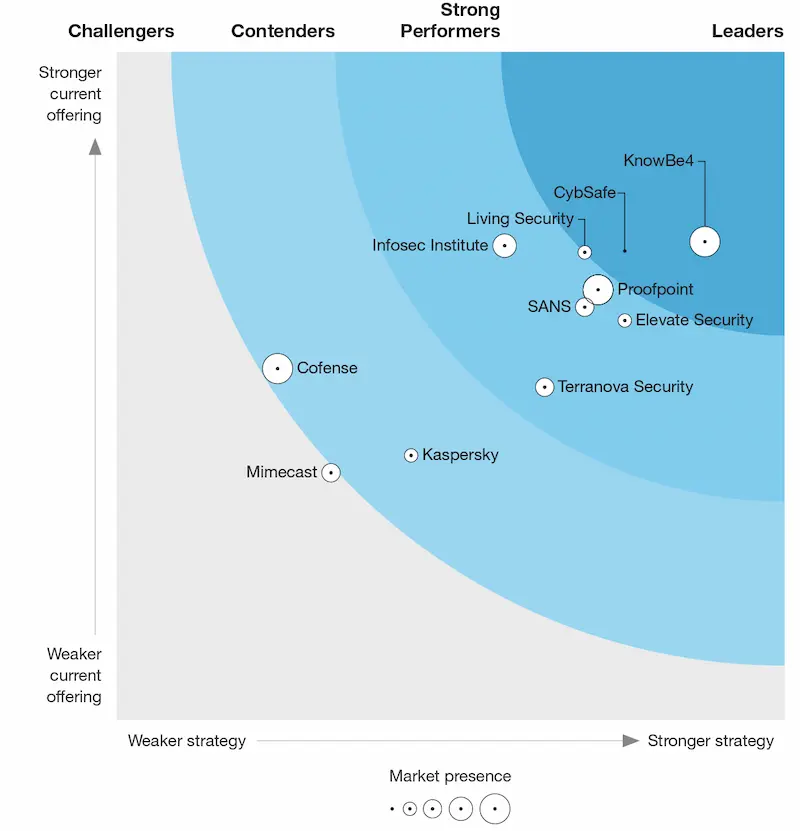
Leaders in human risk quantification
CybSafe has been named a leader in the Forrester Wave™: Security Awareness and Training Solutions, Q1 2022.
The Forrester Wave™ evaluates and compares market players, and CybSafe received the highest possible score in ten criteria, including:
- security behavior;
- human risk scoring;
- security culture betterment;
- reporting capabilities; and
- product vision.
Integrations
CybSafe has extensive integration options for security solutions and IAM providers. Our open APIs can ingest data and export it to other tools in your technology stack.
What your peers say
CybSafe is just another level. It gives us really robust metrics that help us measure where our people are. It shows their behaviors as well as their attitudes.
Caroline Bansraj
Chief Security Office

Having the data and metrics available has allowed us to confidently make informed decisions and get tangible results regarding employee vigilance. We can now focus on the right areas and track our progress whilst doing so.
Alexandre Pieyre
Group Information Security Leader

CybSafe has allowed us to identify changes in security behaviour and respond accordingly. We now see and understand aspects of our human cyber risk that we simply couldn’t get from training & phishing.
Steven Pendleton
Chief Information Security Officer